In this blog, we explore why organisations must assume a cyber incident will eventually occur and focus not only on prevention, but also on building effective cyber resilience. We discuss the importance of having clear incident response plans in place, regularly exercising those plans based on risk, and making informed decisions during an incident to contain attacks and minimise operational disruption. The blog also highlights the role of clear, well planned communication and resilient systems in maintaining business continuity and preserving stakeholder trust in the event of a breach.
Cyber security should always be a high priority for organisations of all sizes, and robust measures to prevent an attack are vital in reducing exposure to threats. In our blog Strengthening Your Cyber Defences: Practical Steps for Every Business, we highlighted the key steps you can take to reduce the likelihood of your organisation suffering a breach, all of which are crucial to safeguarding your organisation against attacks.
However, no organisation can eliminate the risk of a breach entirely. Attack techniques are constantly evolving, vulnerabilities emerge unexpectedly, and human error is inevitable. As such, your organisation must operate on the assumption that a cyber incident will occur at some point: it is not a matter of if, but when. By shifting the focus to resilience as well as prevention, you will not only reduce the likelihood of an attack, but also ensure that your organisation can withstand and recover from incidents when they do arise.
Incident Response
It’s essential to have an understanding of the actions you will take if an incident occurs. This begins with ensuring incidents can be effectively identified and reported in the first place, so staff should feel encouraged to report things that look suspicious.
However, identification is only the first step; once an incident is reported, what happens next? How do you respond and recover? Only 30% of respondents to the Department for Science, Innovation and Technology’s (DSIT’s) Cyber Security Breaches Survey 2025 have a formal incident response playbook (a defined set of instructions outlining what to do in an incident), suggesting that many organisations lack an appropriately detailed understanding of how they would respond if an incident occurred. Creating and implementing formal, detailed response plans is the most effective method of ensuring your organisation has that understanding. For more information on creating effective incident response plans, read our blog on How to Develop a Robust Business Continuity Plan.
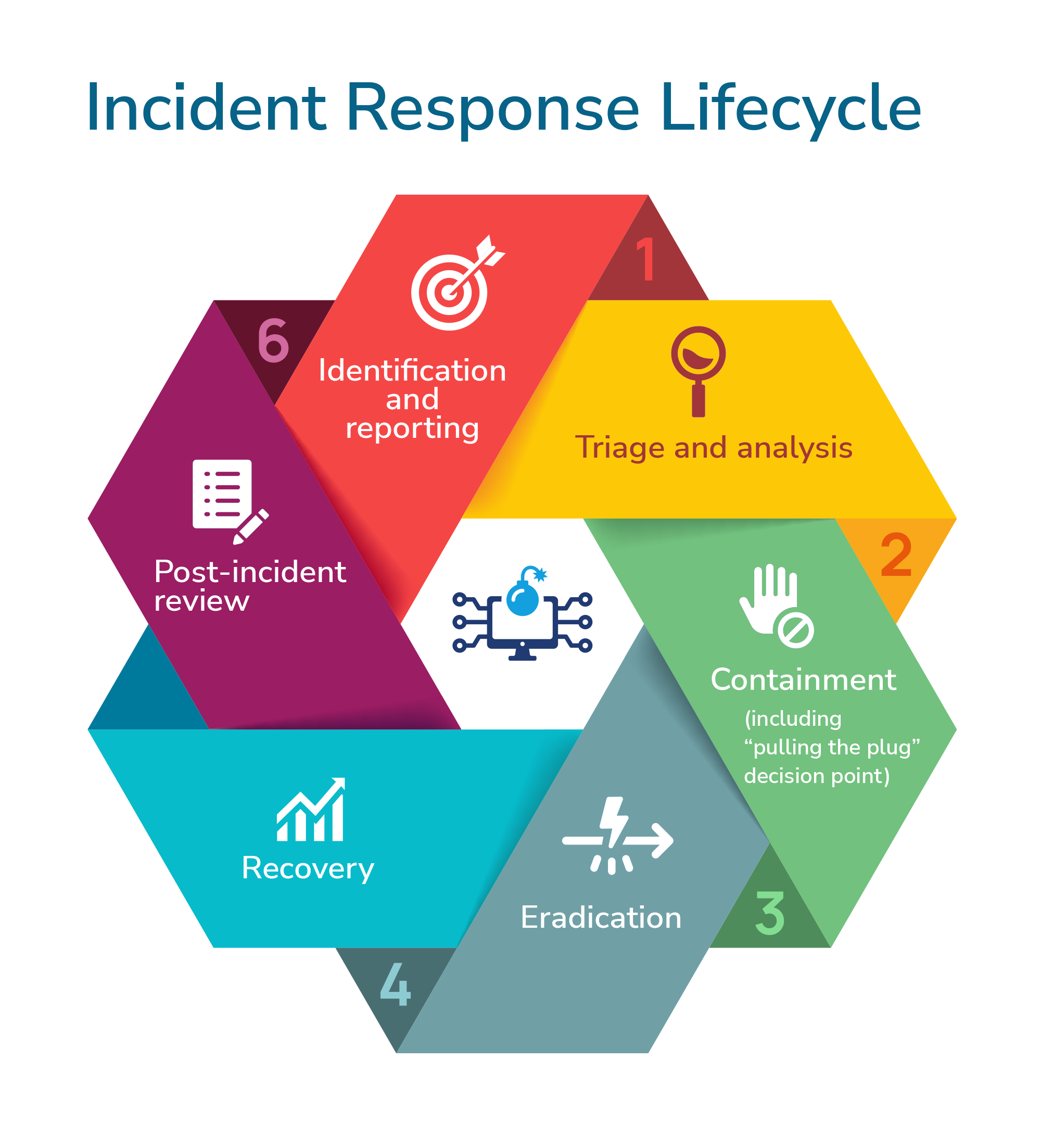
Exercising Plans
To minimise the impact of a breach or disruption if one occurs, it’s essential to regularly test your business continuity plans (BCPs) and other incident response plans through structured exercises. Our blog on Business Continuity Exercising provides detailed guidance on what BC exercising is, the different types available and how to conduct them effectively. However, in short, an exercise is an activity where you practise using your BCPs, often in the form of tabletop simulations (where your team works through a realistic scenario and simulates their response) or documentation walkthroughs (where teams review their plans together to ensure alignment), although there are a number of other exercise types available. The outputs of these exercises will allow you to determine the effectiveness of your plans and identify any areas for improvement, without the high stakes of a genuine incident.
When deciding which elements you need to prioritise for exercising, one key consideration should be your risk assessment. Risks are incidents that haven’t happened yet, so if your risk assessment has identified highly likely and/or impactful risks, those scenarios should be exercised first and revisited most frequently to ensure preparedness is strongest where it matters most.
Disconnecting to Contain an Attack
If a cyber attack incident does occur, the quickest and most effective way of stopping the attack may be to ‘pull the plug’, i.e., cut off your organisational environment’s access to the internet. However, while cutting off your environment may halt the attack, it will also halt any genuine access by your staff, customers, etc., potentially leading to devastating consequences for your organisation. If faced with this choice, you will need to weigh up the cost and impact of the incident itself against the impact of your customers losing access; once the impact of the incident outweighs that of customers not having access, pulling the plug may be the most appropriate option. These are decisions and considerations you need to make in advance, which is why detailed response plans and processes need to be in place.
Communication
During an incident, you will need to keep key stakeholders (e.g., clients, staff, media, and regulators) informed. In an information vacuum, people speculate and rumours develop, so providing communications and updates allows you to maintain control of the narrative around the incident. Such communications need to be appropriate and tailored to their intended audience, providing only the information they need and not sharing unnecessary technical or sensitive details. Again, these communications processes can (and should) be planned in advance, giving you the opportunity to determine when specialist support, such as from PR firms and legal advisors, may be required.
Maintaining Business Continuity and Stakeholder Trust
One of the most harmful impacts of an incident is reputational damage and loss of trust, which can partially stem from services being unavailable during an incident. To counter this, you should put yourself in a position to continue operations and maintain service availability (to the greatest extent possible), even while an incident is occurring in the background. To do so, build redundancy and resiliency into your systems, so that critical services can continue running even if part of your environment is compromised.
Closing Thoughts
Cyber security is no longer just about preventing attacks, but also being ready to respond when they occur. By combining strong preventative controls with well defined, regularly exercised response and recovery plans, organisations can significantly reduce the operational, financial and reputational impact of a breach. Ultimately, resilience puts your organisation in the strongest possible position to withstand incidents and maintain the trust of your stakeholders.
How URM Can Help
With our heavily ISO 22301-aligned approach, URM can provide BC services and guidance that are informed by both recognised best practice and extensive practical experience. For example, our business continuity consultants can assist with your business impact analysis (BIA), the foundation of the BC planning process. With our BIA support services, we will help establish your BIA methodology, providing you with a clear picture of what you will need to recover first in the event of disruption, how quickly, and to what level. You can also utilise our BIA tool, Abriska® 22301, which simplifies the BIA process and helps you create your BC plan.
Having conducted the BIA, URM can also help you to develop and implement bespoke BCPs or IMPs. Once these have been developed and you are ready to conduct a business continuity exercise, we can devise challenging, tailored scenarios to exercise your plans and provide a report on your team’s response with any recommendations for improvement.
If you are looking to certify to ISO 22301, URM can guide you through the entire process, from conducting a BC gap analysis to providing implementation and remediation support, ensuring you are prepared for a successful assessment.
URM is pleased to provide a FREE 30 minute consultation on penetration testing for any UK-based organisation.
If you are unsure, URM can perform CREST-accredited internal and external penetration testing against all IP addresses associated with your organisation, location, or service.
Designed to assess the architecture, design and configuration of web applications, our web application pen tests use industry standard methodologies to identify vulnerabilities.

URM’s blog discusses upcoming changes to Cyber Essentials, including the changes seen in the Willow Question Set and how they may impact your organisation.

URM’s blog explains the measures the Bill will introduce, the entities it will bring into regulatory scope & what the Bill could mean for your organisation.

URM’s blog breaks down the latest changes to the Cyber Essentials requirements and outlines why these updates matter for organisations seeking certification.



