In this blog, we explore the internal weaknesses that commonly leave organisations exposed to cyber threats. We discuss how governance, culture, technology and supply chain oversight each play a critical role in building effective defences, and highlight practical, cost efficient steps that organisations can take across each of these areas to strengthen their security posture.
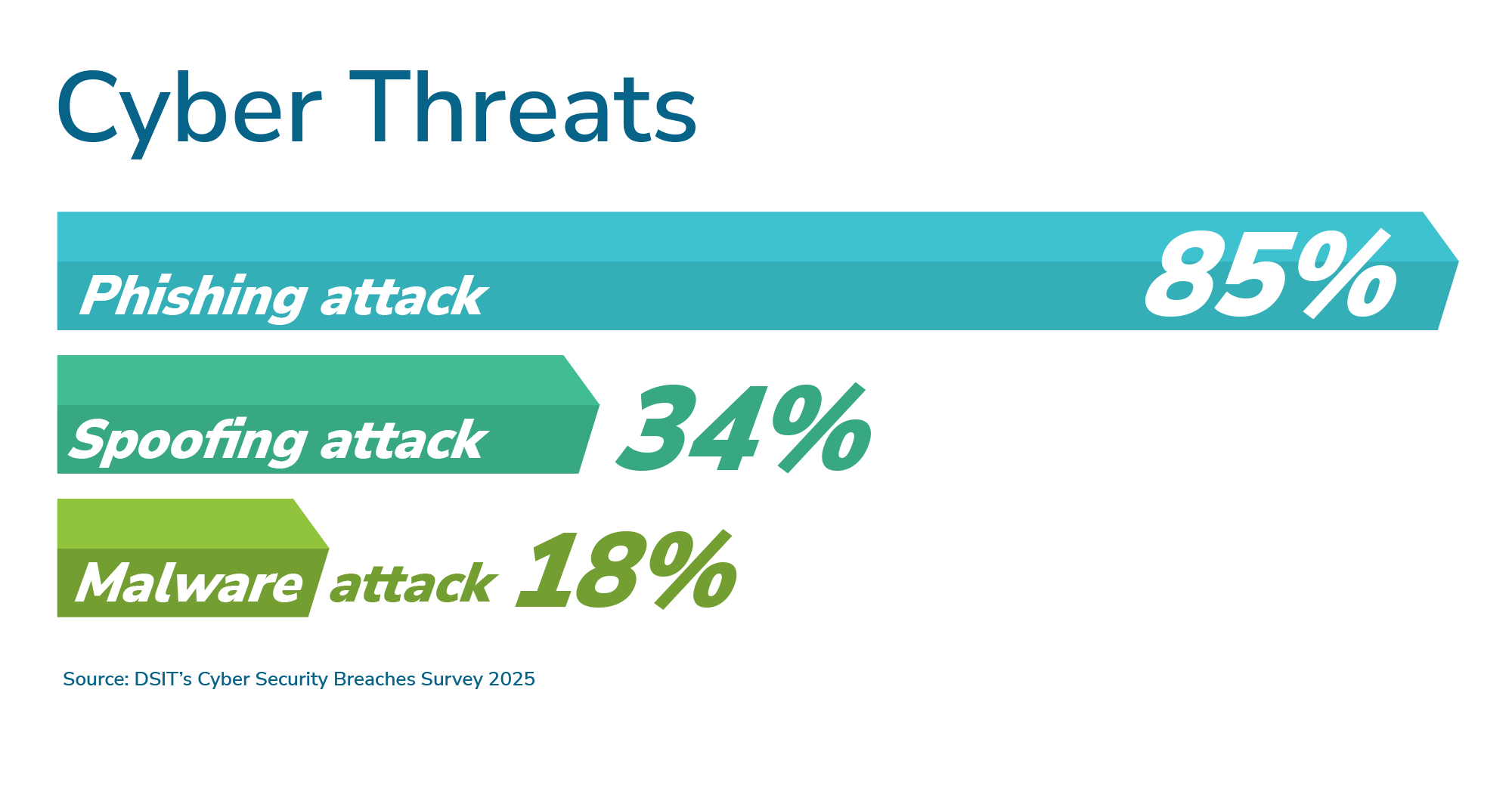
Cyber threats are continuing to escalate. In recent years, headlines have been filled with major organisations brought to a standstill by cyber incidents that have cost billions and eroded public trust, and survey data has further demonstrated just how widespread and disruptive these attacks have become. According to the Department for Science, Innovation and Technology’s (DSIT’s) Cyber Security Breaches Survey 2025, 85% of organisations experienced a phishing attack in the previous year, while 34% reported impersonation or spoofing attacks. Malware attacks, reported by 18% of respondents, also remain a persistent danger.
For organisations that suffer these attacks, the consequences can be severe and far reaching. Beyond immediate disruption, breaches can result in prolonged operational downtime, compromised sensitive information, regulatory penalties, and lasting reputational damage. Individuals involved in response and recovery often endure long hours, intense pressure, and customer/leadership stress, resulting in mental-health strain, burnout risk, and feelings of personal accountability.*
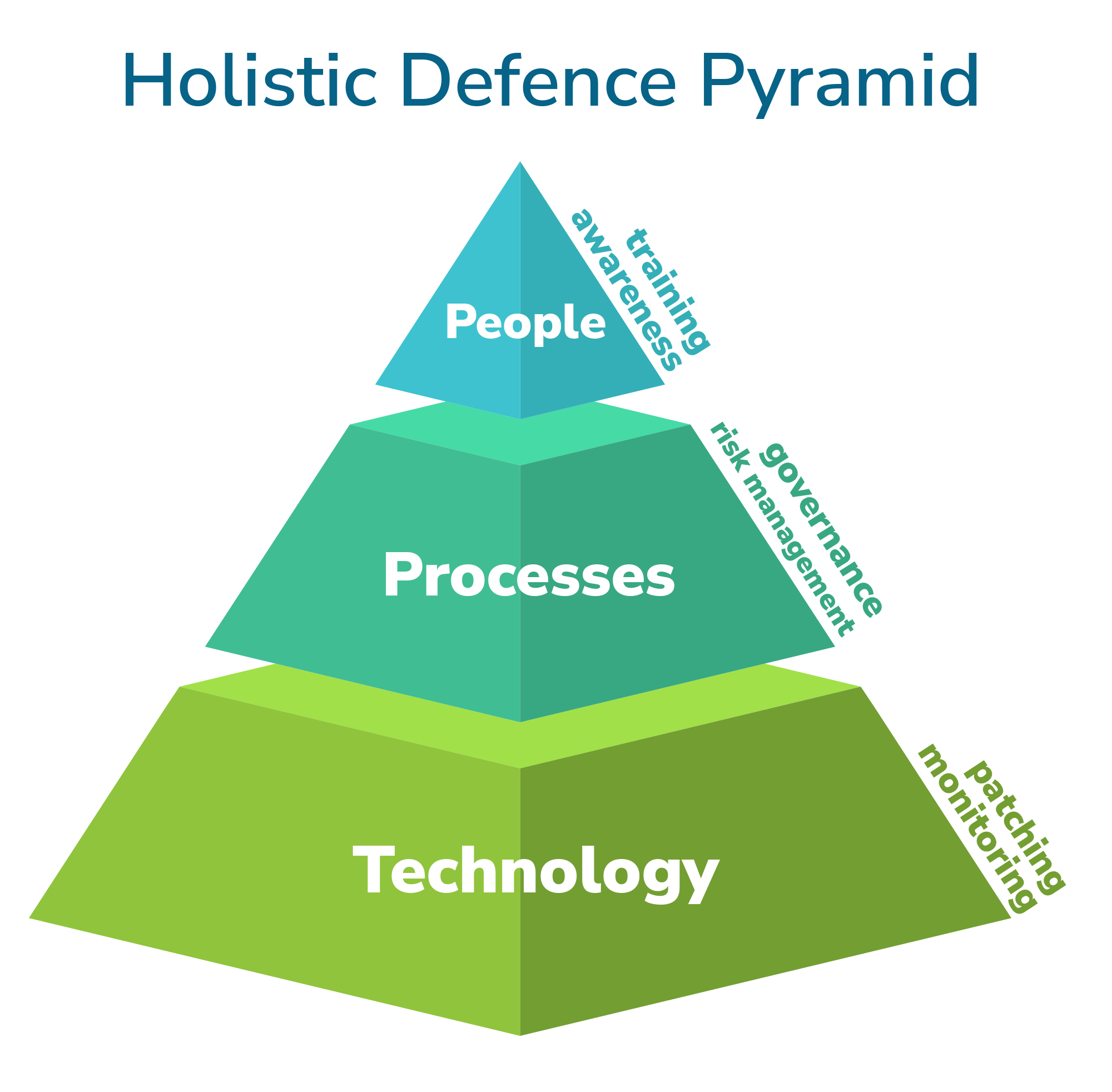
In this landscape, cyber security becomes a strategic, organisation-wide challenge, requiring robust governance, effective controls, and a culture of awareness. Only by embedding security into everyday decision making can your organisation ensure it is protected in this increasingly hostile threat environment.
*To learn more about the real-world impact of cyber breaches on individuals, read our blog Cyber Security Case Study: The Human and Organisational Cost of a Breach.
Common Cyber Security Weaknesses and Emerging Risks
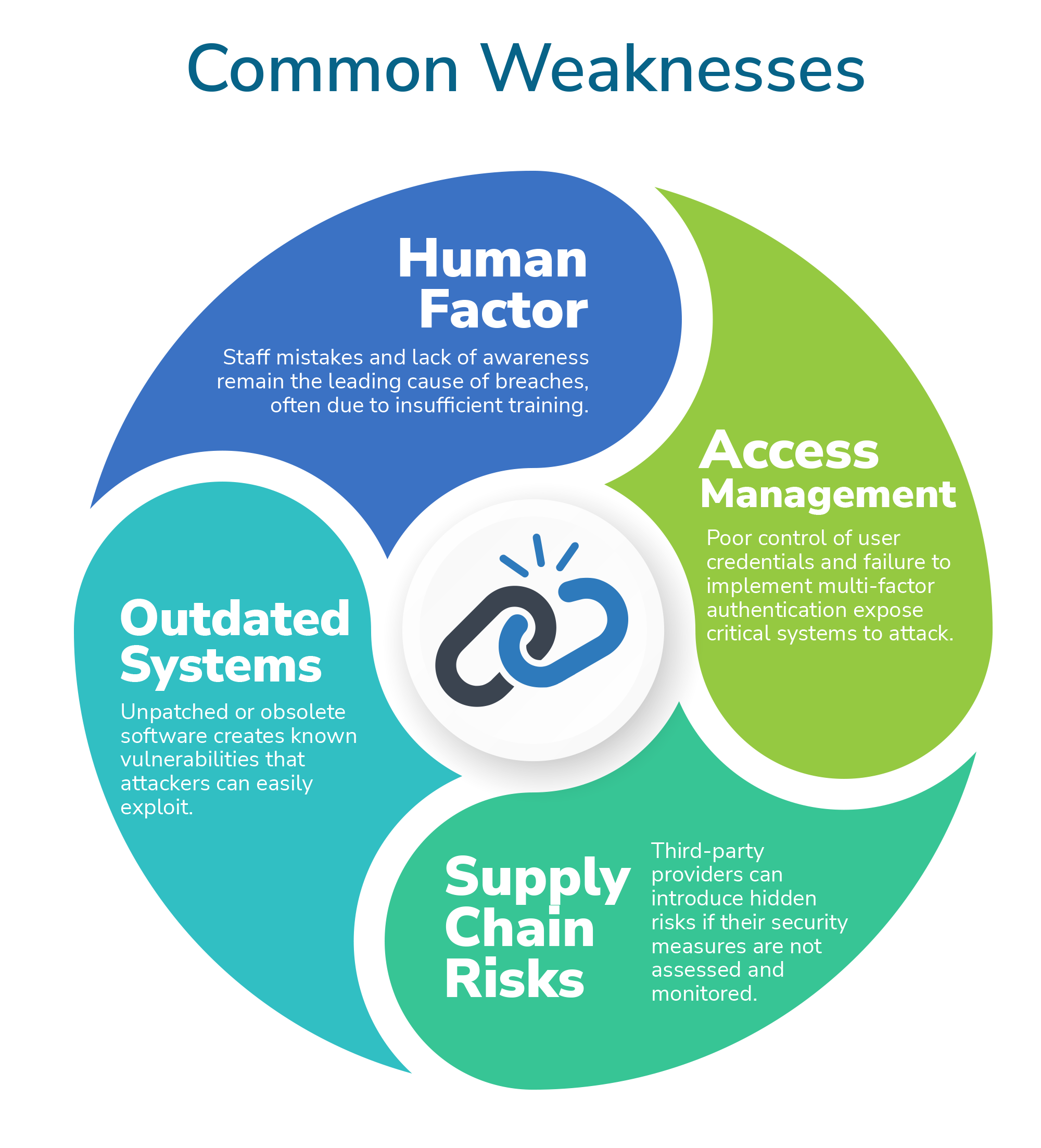
Many successful attacks exploit long‑standing internal weaknesses that organisations struggle to address. Understanding these underlying issues is crucial, and without tackling them, security gaps persist and leave you exposed.
The following sections explore some of the most common areas of weakness we come across.
The human factor
People remain the most persistent and significant vulnerability in an organisation’s security posture. While some breaches result from deliberate actions by malicious insiders, most are caused by genuine mistakes or a lack of knowledge. Human error rarely occurs in isolation however; it is often linked to underlying issues such as staff failing to follow procedures or insufficient training and awareness.
The latter is a particularly widespread issue, with the Cyber Breaches Survey finding that only 19% of businesses provide regular cyber security training to staff. Given that phishing attacks, in particular, are becoming increasingly sophisticated and difficult to spot due to the advent of artificial intelligence (AI), equally sophisticated, up-to-date and regular training is now a necessity.
Access management
Poor access management is another area of weakness we frequently identify, such as failing to ensure appropriate user credentials are in place for different systems. At the most basic level, this involves implementing rules around the length and complexity of passwords that make them harder to guess and compromise. While this is important, current best practice is to also implement multi-factor authentication (MFA), i.e., requiring two or more verification types to confirm a user’s identity before granting access. However, uptake remains limited, with only 40% of organisations reporting that they have applied MFA across their critical systems.
Weaknesses in starters, movers, and leavers processes are common, with the movers stage often overlooked. As a result, employees who change roles frequently retain access they no longer need, increasing the risk of privilege creep and unnecessary exposure, thereby creating an avoidable security risk.
Outdated or unpatched software and systems
Failing to patch or update software and systems is a significant risk. When software is out of date, it often means a known vulnerability exists that an attacker can exploit to infect your environment with malware.
Nearly a third of businesses report failing to apply software updates promptly. In many cases, this stems from organisations not having full visibility of the software that exists within their environment, meaning outdated or unused software goes unnoticed and unpatched. To address this, you need to maintain a comprehensive inventory of all software present in your environment and implement a consistent, organisation-wide process for monitoring, patching, and updating it.
Supply chain risks
The Cyber Breaches Survey reports that only 13% of businesses assess supplier security risks, even though use of third-party services, especially cloud services, is increasing. This shows that many organisations are still unaware of the security risks suppliers can introduce. Different suppliers create different levels of risk depending on the access they have to your systems and data, so you should consider carefully how much access they truly need. For example, if a supplier asks for admin access, check whether this is genuinely required. Minimising access and limiting technical integration reduces the chance of a compromise being passed on to your organisation.
You also need a clear view of the security measures your suppliers have in place. Supplier questionnaires are one way to gather this information. Suppliers with access to your systems or sensitive information may need to be treated as high risk and given a questionnaire or other screening. Those with no access may be low risk and potentially not need a questionnaire at all because the risk is already reduced.
Large service providers such as Microsoft or AWS often cannot complete supplier questionnaires. In these cases, review their terms and conditions to check whether their security measures meet your needs. If they do not, you may need to purchase additional security options from them.
Reducing the Likelihood of a Cyber Breach
The following sections examine some of the most effective strategies for minimising the risk of a cyber breach.
Governance
Risk-based approach
Adopt a risk-based approach to cyber and information security, as this will allow you to more effectively protect assets and ensure prioritised, cost-effective remediation. This process needs to start from a position of understanding what assets you have, and where they are. Are they in databases, on the C: drive of staff laptops, or being processed by applications? Once you have this visibility, you can assess the potential impacts if something were to go wrong.
These may be:
- Confidentiality breach – unauthorised access to sensitive information
- Integrity impact – information being altered without permission or not kept accurate
- Availability issue – systems or data not accessible to those who need them.
Once you know the type of impact that is relevant to each asset, you will need to understand the importance of that impact, e.g., how important is it to protect a particular information asset from a breach of confidentiality? Ask the same question for the different impact types across all of the different information assets you’ve identified. You will then be able to consider what could cause those impacts, and the steps you can take to mitigate those risks. Without a comprehensive awareness of the assets you have and where they are, you will struggle to conduct those later stages of the risk management process effectively.
Continuous risk management
In the past, organisations would often carry out a single annual risk assessment and not revisit this until the following year. However, best practice has evolved considerably due to the use of technology, third parties, increasing attack sophistication, etc. You now need an ongoing, continuous understanding of the threats you face to identify any changes that impact your risk profile, and whether your approach needs to be adjusted as a result. This doesn’t mean conducting formal risk assessments every day. It is about maintaining an ongoing awareness of emerging threats and ensuring processes are in place to analyse and evaluate that information effectively. This will enable you to determine which threats you need to respond to, and which can be ignored or deprioritised.
Identify vulnerabilities
As noted above, systems become outdated over time. Checking a version number will show that a system is out of date, but it will not tell you what weaknesses this creates or what the practical impact might be if the system is not updated. Understanding these points helps you decide what to fix first. If a system is out of date but not exposed to any real threats, it is likely to have lower impact and likelihood, and can be given a lower priority.
Ineffective technology and tools is another vulnerability we frequently encounter. For example, many organisations have antivirus solutions that haven’t been configured properly, leaving gaps that attackers can easily bypass. To reduce this risk, you need to understand the capabilities of your tools and assess and improve that capability over time.
Conducting regular penetration testing and vulnerability scanning is an effective way of identifying vulnerabilities, but these are not the only options available. If you have assets that you don’t know how to assess, engaging a third-party specialist can provide clarity. They can work with you to evaluate those areas and help strengthen the security of assets that may otherwise go overlooked.
Monitor and measure
To safeguard your organisation against threats, you will need to implement a range of security controls, such as formal policies and processes, technical controls, physical security measures, etc. However, implementing these controls is only the starting point. It is not enough to assume they will continue to operate effectively; you must regularly assess their performance and identify where improvements are needed.
This requires ongoing monitoring and measurement of control effectiveness. Monitoring should be frequent and consistent enough to reveal trends and highlight when a control’s performance is deteriorating, allowing you to adjust or replace it before security gaps emerge.
Culture
As noted earlier, your staff are one of your most significant security risks. To mitigate this risk, your organisation needs to foster security responsibility at all levels. The first port of call in cultivating a security-conscious culture is training. While many organisations provide cyber security training during induction, this alone is insufficient to build the awareness needed to counter today’s sophisticated and pervasive threats
Instead of just providing cyber security training to staff during induction that is never updated or delivered again, URM believes a more dynamic approach needs to be taken. Organisations should maintain awareness of the evolving threat landscape and update training regularly to reflect these changes. This training should be delivered to all staff at least once a year. Between annual sessions, organisations should also send awareness emails or newsletters to inform employees of new threats or attacks they need to be aware of. Social engineering (phishing) simulations can also be beneficial for assessing how well staff can spot and report suspicious emails in practice, providing insight into where additional guidance may be needed and helping embed a stronger culture of vigilance across the organisation.
You should look to incorporate some form of knowledge testing into training, such as a quiz at the end to test understanding of key points. This not only confirms that staff have actually absorbed the material, but also helps you to identify any shortcomings in the training content if, for example, there’s a particular question consistently being answered incorrectly.
Role-specific training can be useful for some teams. For example, finance teams need guidance on handling payment information safely, while IT teams may need extra training on technical security. Providing targeted support helps staff gain the specific knowledge they need to manage the risks linked to their roles.
Technology
From a technical perspective, URM strongly advocates continuous monitoring, regular patching and layered protection. Controls need to cover people, processes, procedures, technical measures and physical security, and critical systems and processes should be actively monitored. Logging and alerts are often overlooked because responsible teams are overstretched and dealing with competing priorities. However, it is important that time and resources are set aside to review logs and alerts, and to take follow up actions where issues are identified.
URM often observes organisations repeating the same penetration tests each year without adjusting the scope or type of testing. This is perfectly acceptable if the goal is to meet compliance or contractual requirements, but it rarely leads to significant security improvements. A business led approach, where the test scope is flexible and shaped around your organisation’s concerns and risks, can provide far more valuable insight. This does not necessarily increase costs, but it does offer a clearer view of your security posture and opportunities to strengthen it.
Supply Chain
The main purpose of supplier due diligence is to understand the risk of working with a particular third party. Your supplier questionnaires need to provide you with a full picture of this risk, including how the supplier manages its own supply chain. This helps you judge whether they understand and control risks from their third parties, which could otherwise affect your information and systems.
You should also consider what you expect from the supplier, the nature of your relationship with them, and the types of risks that may arise. For example, where is the sensitive information they may access physically located? Are you sending information to an overseas organisation, and is this appropriate? If the supplier uses round the clock support teams based abroad, is it acceptable for those teams to have access to your systems?
You will also need to think about how you would end the relationship if required. This means having an exit plan that sets out how any information held by the supplier will be returned or securely destroyed.
Closing Thoughts
The cyber security threats and challenges facing organisations today are significant, but not insurmountable. By taking a holistic approach to cyber security and viewing it as not just a technical exercise, but an organisation-wide responsibility that spans people, processes and culture, your organisation can build the security posture needed to withstand an increasingly complex threat landscape.
How URM Can Help
If your organisation would benefit from enhancing its cyber security and risk management programme, URM can provide tailored support to help reduce your susceptibility to attacks.
Governance and risk management
Having supported hundreds of organisations’ risk management programmes over the last 20 years, URM is the ideal partner to help you create and implement an effective risk management plan. With our proven information security risk management software, Abriska 27001, we can support the entire risk assessment process, as well as assisting with risk treatment and helping you prioritise treatment activities to maximise your time, effort and budget. Whether you are looking to establish and implement an ISO 27001-aligned information security management system (ISMS) or simply enhance your organisation’s risk management capabilities, URM will provide tailored guidance and support that is suited to your organisation’s unique needs.
In terms of supply chain risk, one of the greatest challenges of conducting supplier risk management is the administrative burden and possibility for human error when assessing numerous third parties. Abriska 27036, URM’s supply chain risk management tool, is the ideal solution for organisations that have numerous suppliers with varying risk levels. Our software enables you to tailor your supplier questionnaire to ensure only relevant questions are sent to each supplier, as well as allowing you to ask more in-depth questions of higher risk suppliers, whilst also improving efficiency by automating the distribution and analysis process.
Penetration testing
As a CREST-accredited provider of penetration testing, URM can offer a range of pen testing services to identify the vulnerabilities affecting your environment and assets before they can be exploited. For example, we can offer network and infrastructure penetration testing against all IP addresses associated with your organisation, location or service from either an internal or external perspective. We can also conduct cloud penetration testing, web and mobile app testing, as well as business-led pen testing, in which the scope of the penetration test is determined by your organisation’s unique issues and concerns.
URM is pleased to provide a FREE 30 minute consultation on penetration testing for any UK-based organisation.
If you are unsure, URM can perform CREST-accredited internal and external penetration testing against all IP addresses associated with your organisation, location, or service.
Designed to assess the architecture, design and configuration of web applications, our web application pen tests use industry standard methodologies to identify vulnerabilities.

URM’s blog highlights the growing threat to cyber security in the UK and the importance of the Cyber Essentials scheme in mitigating these risks.

URM’s blog provides 3 useful top tips to help your organisation prepare for successful Cyber Essentials or Cyber Essentials Plus certification assessment.

URM explains each control law firms must include in an information management and security policy that complies with the Lexcel Practice Management Standard.



