In this blog, we explore Clause 5.1 of ISO 27001, which sets out the need for visible and active leadership commitment to an organisation’s information security management system (ISMS). We explain the specific areas where top management needs to demonstrate accountability and support, why this involvement is critical to achieving certification, and how organisations can evidence leadership engagement to auditors.
Clause 5.1 (Leadership and Commitment) of ISO 27001 emphasises the importance of information security being supported, both visibly and materially, by senior management. This Clause identifies specific aspects of an ISMS where top management is expected to demonstrate both leadership and commitment.
What does conformance to Clause 5.1 involve?
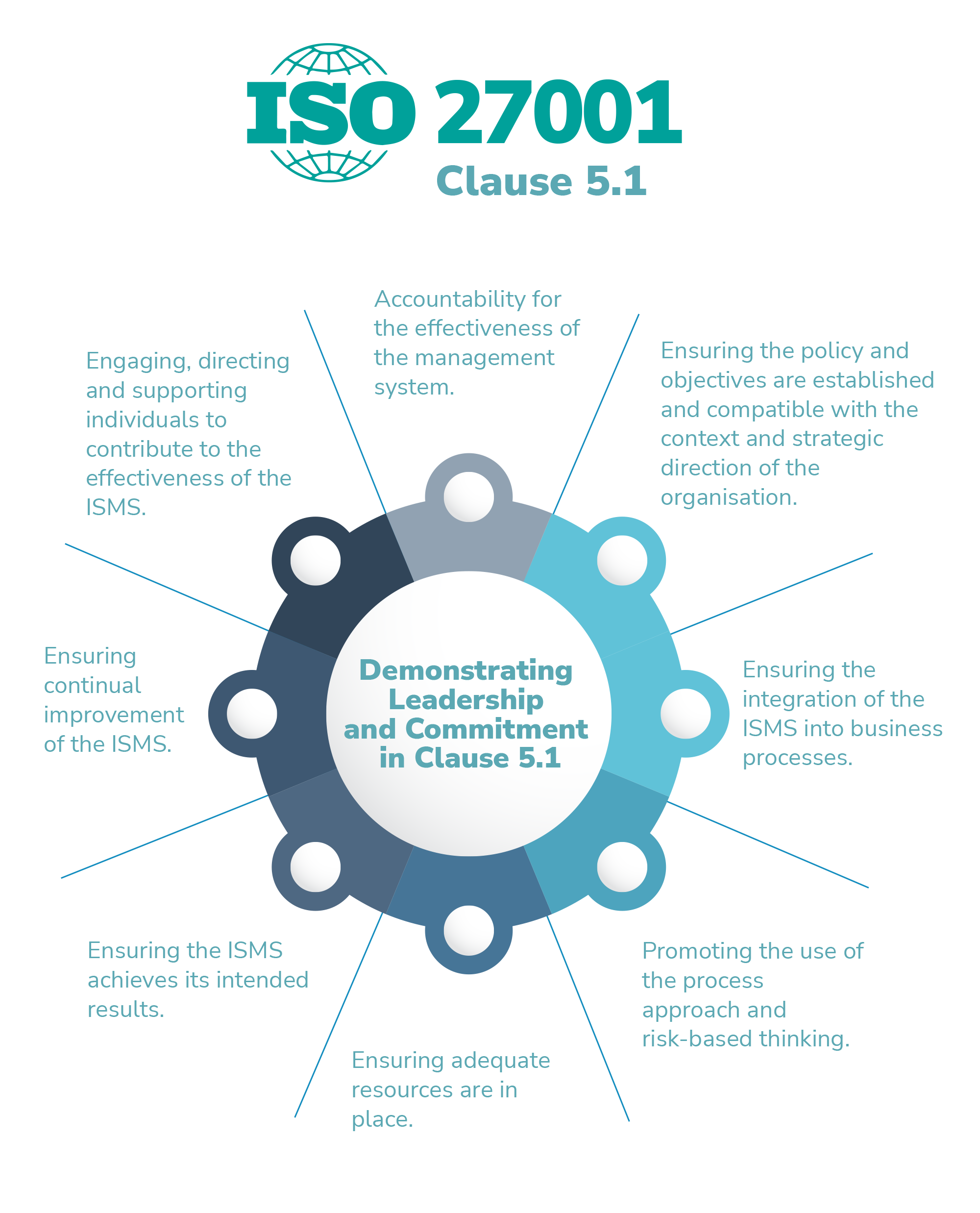
Clause 5.1 identifies specific aspects of the ISMS where top management needs to demonstrate both leadership and commitment. These aspects and examples of how they can be evidenced include, but are not limited to:
Accountability for the effectiveness of the management system. This can be demonstrated through leadership attendance at management reviews and opening / closing meetings for audits, involvement with the planning and establishment of the ISMS, and regularly communicating the importance of information security via town hall meeting, emails or intranet updates.
Ensuring the policy and objectives are established and compatible with the context and strategic direction of the organisation. Examples of acceptable evidence include leadership selection of information security objectives and regular review and monitoring of the performance of the objectives, as well as leadership approval of information security policies.
Ensuring the integration of the ISMS into business processes. Leadership can demonstrate this by ensuring that security is woven into the organisation’s day-to-day activities. For example, leadership may be involved in ensuring that information security controls are embedded in product development, HR, procurement and operational processes.
Promoting the use of the process approach and risk-based thinking. This can be demonstrated by adopting a robust risk assessment methodology built on the information security pillars of confidentiality, integrity and availability (CIA). Leadership can further demonstrate commitment here by being actively involved with reviewing information security risks and risk treatment plans. (To learn how to establish a risk assessment methodology and conduct a risk assessment in line with the Standard’s requirements, read our blog on Information Risk Assessment and Treatment in ISO 27001.)
Ensuring adequate resources are in place. Here, conformance can be evidenced by leadership allocating day-to-day responsibility for the ISMS to competent personnel (e.g., an information security manager), and by these employees having leadership’s full support. Leadership can also ensure adequate resourcing by endorsing technology designed to improve security and efficiency of the ISMS, and the use of approved third parties as competent resources if the organisation does not have sufficient capability to implement and maintain an effective ISMS itself.
Ensuring the ISMS achieves its intended results. Leadership can demonstrate this through involvement in management review meetings, ownership of actions resulting from the management review that are raised to continually improve the ISMS, and mandating security awareness training and participating in it themselves.
Ensuring continual improvement of the ISMS. This can be evidenced by leadership acting on audit findings, feedback from interested parties or incident reports designed to improve the performance of the ISMS.
Engaging, directing and supporting individuals to contribute to the effectiveness of the ISMS. Leadership’s ownership of, and active support for, each of the above responsibilities serves as evidence of this commitment. In addition, by promoting compliance and accountability, leadership ensures that the organisation meets all information security–related legal, regulatory, and contractual obligations.
Why do leadership and commitment matter?
Information security management must be compatible with your organisation’s business objectives and processes for it to work in practice, and without leadership support, any ISO 27001 certification project will struggle to get off the ground. URM has produced several ISO 27001 case studies, and when organisations are asked about the key factors behind successfully implementing the Standard and achieving certification, the support and commitment of senior management are consistently cited as one of the most important contributors.
If leadership is not actively involved in your ISMS, such as not participating in management reviews or being unable to demonstrate to an external auditor that there is a leadership representative taking responsibility during an audit, your organisation will not be conformant to ISO 27001 and will be unable to certify against the Standard. Auditors often emphasise that the spirit of ISO 27001 must come from the top; if leadership involvement is not evident, they are likely to scrutinise the ISMS more rigorously and with greater scepticism during the audit.
However, an engaged and supportive leadership will provide confidence to an external auditor that your organisation is serious about information security. As such, it is essential that you can demonstrate leadership commitment to the ISMS along with leadership involvement, such as in management reviews, broader ISMS decision making, and the required annual external audits for ISO 27001. This commitment can be evidenced through documentation and records, e.g., management review meeting notes and top management communications.
Closing Thoughts
Clause 5.1 represents an essential element of any successful and effective ISMS. As well as being a requirement for conformance to the Standard, commitment and support from leadership ensure that information security is embedded across the organisation, aligned with business objectives, and subject to continual improvement.
How URM Can Help
With 2 decades of experience assisting organisations’ ISO 27001 implementation, URM is the ideal partner to support any aspect of your organisation’s conformance/certification to the Standard. Our team consultants can offer a wide range of consultancy services to help you fully conform to ISO 27001 requirements. We can conduct a gap analysis where we establish your current level of conformance, and help you conduct your risk assessment using our proven risk assessment tool, Abriska 27001. Following this, we can support your development of policies, processes and ISMS infrastructure that are aligned with both the Standard’s requirements and your organisation’s unique needs. URM can also offer a range of internal audit services, including conducting an internal audit ahead of your certification assessment to ensure your organisation is conformant, planning and implementing a full 3-year ISO 27001 audit programme, or auditing more specific aspects of the ISMS or particular controls.
In addition to our consultancy services, URM regularly delivers ISO 27001-related training courses. Our Introduction to ISO 27001 Course explores all aspects of information security and the importance of ISO 27001 in protecting information, whilst our Certificate in Information Security Management Principles (CISMP) Training Course will fully prepare you to sit and pass the BCS invigilated examination and gain an industry-recognised information security qualification.
URM can help you achieve ISO 27001 certification
Unsure whether your ICT risk framework meets DORA standards? Our experts will carry out a detailed gap analysis and provide clear, prioritised steps to help you achieve full compliance.
Our consultants will evaluate your organisation against DORA’s core requirements. Gain practical insights to strengthen your digital resilience and meet regulatory expectations.

What are the Benefits of Implementing ISO 27001? We dig a bit deeper on the benefits that are gained from implementing the standard.

With this blog, the spotlight turns to internal audit and specifically in the context of ISO 27001, the International Standard for ISM.

As with all ISO standards, it has been developed by a panel of experts and provides a specification for the development of a ‘best practice" ISMS



