In this blog, we will explore the key provisions of the European Union (EU) Cyber Resilience Act (CRA), outlining which entities and products it applies to, the risk-based classification of products, and the essential cyber security requirements that must be met. We’ll also break down the specific obligations for manufacturers, importers, distributors and open-source software stewards, explain how the CRA aligns with the EU AI Act, and highlight the potential penalties for noncompliance.
The Cyber Resilience Act (CRA) is a new EU regulation aimed at improving the cyber security of products with digital elements (PDEs) across the European market. Whether you're a manufacturer, importer or distributor of these products, the CRA introduces new responsibilities and significant consequences for noncompliance.
What is the CRA and Who Does it Apply to?
The Cyber Resilience Act (2024/2847) is a regulation that introduces mandatory cyber security requirements for all PDEs sold on the EU market.
The CRA defines a PDE as a ‘software or hardware product and its remote data processing solutions, including software or hardware components being placed on the market separately’. Specifically, the Act applies to PDEs that are ‘made available on the market, the intended purpose or reasonably foreseeable use of which includes a direct or indirect logical or physical data connection to a device or network’.
Essentially, the CRA regulates any digital product or part (that does not fall under one of the Act’s exceptions), whether hardware or software, that can connect to something, such as browsers, routers, health monitoring wearables, virtual private network (VPN) products and certain smart devices. The Act applies to both manufacturers of, and importers and distributors of PDEs.
However, the CRA does not apply to PDEs that are already regulated by other, existing regulations, including medical devices, motor vehicles, civil aviation and marine equipment. PDEs developed exclusively for national security and defence purposes are also excluded from the Act’s scope.
The Act aims to:
- Complement pre-existing EU cyber security measures
- Ensure that PDEs on the EU market have limited vulnerabilities,
- Ensure that manufacturers are responsible for the cyber security of PDEs throughout their lifecycle
- Improve transparency of PDE security.
When Does the CRA Come Into Effect?
The CRA entered into force on 10 December 2024, however the applicability of its requirements is staggered across three key dates. The Act’s provisions relating to conformity assessment bodies (Articles 25 to 41) will commence from 11 June 2026, whilst manufacturers’ incident and vulnerability reporting obligations will apply from 11 September 2026. The rest of the CRA’s obligations will become applicable on 11 December 2027, and full compliance with the Act will need to be achieved by this date.
Risk Classification
The CRA categorises PDEs based on their level of risk, with each category being subject to different requirements. PDEs with the lowest level of risk are defined as ‘default’ products, and 90% of PDEs are expected to fall into this category. The next level is ‘important’ PDEs, which are required to undergo specific conformity assessments. Important PDEs are characterised by their performance of functions that are critical to the cyber security of other products, networks or services, or that carry a significant risk of adverse effects in their ability to disrupt, control or cause damage to a large number of other products, or to the health security or safety of users. This category of product is divided into two classes.
Class 1 important PDEs identified by the CRA include:
- Identity management systems and privileged access management software and hardware
- Browsers
- Password managers
- Anti-malware software
- VPN products
- Network management systems
- SIEM systems
- Boot managers
- Public key infrastructure and digital certificate issuance software
- Physical and virtual network interfaces
- Operating systems
- Routers, modems and switches
- Microprocessors and microcontrollers with security-related functionality
- Application specific integrated circuits (ASIC) and field-programmable gate arrays (FPGA) with security-related functionality
- Smart home general purpose virtual assistants
- Smart home products with security functionalities
- Internet connected toys that have social interactive features (e.g., speaking or filming) or that have location tracking features
- Personal wearable products that have a health monitoring purpose or are intended for use by children.
The list of Class 2 important PDEs defined by the Act is considerably shorter, with far fewer products falling into this Class:
- Hypervisors and container runtime systems that support virtualised environments
- Firewalls, intrusion detection and prevention systems
- Tamper-resistant microprocessors
- Tamper-resistant microcontrollers.
Due to their higher risk, Class 2 important PDEs are subject to more rigorous compliance assessment requirements than Class 1 PDEs. Whilst the conformity of Class 1 PDEs can be self-assessed by manufacturers (providing certain conditions are met), Class 2 products must be assessed by an external third party.
The final category defined by the Act is ‘critical’ PDEs. These are products deemed to have the highest level of risk and, as such, are required to have either a European cyber security certificate of at least a ‘substantial’ assurance level. A PDE will fall into the critical category if there are essential entities with critical dependency upon it, or if incidents and exploited vulnerabilities concerning the PDE could lead to serious disruptions of critical supply chains across the internal market.
The Act defines PDEs in the critical category as hardware devices with security boxes (i.e., devices used to capture, protect and transfer data securely), smart meter gateways within smart metering systems and other devices for advanced security purposes (such as secure crypto-processing), and smartcards or similar devices.
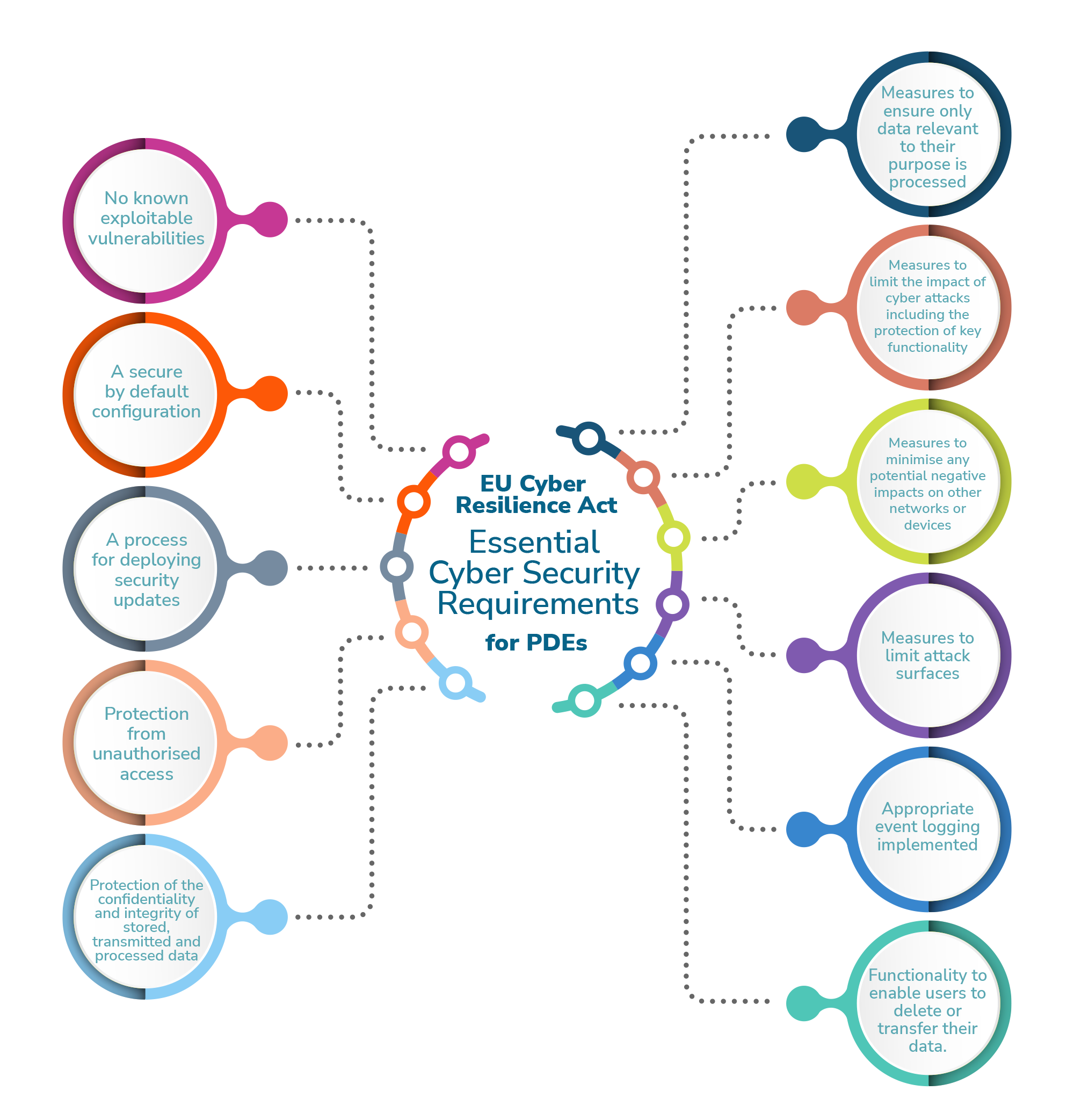
What Are the Essential Cyber Security Requirements?
The essential cyber security requirements defined by the Act state that PDEs shall include cyber security protection appropriate to their level of risk. Where applicable, this should mean they have:
- No known exploitable vulnerabilities
- A secure by default configuration
- A process for deploying security updates
- Protection from unauthorised access
- Protection of the confidentiality and integrity of stored, transmitted and processed data
- Measures to ensure only data relevant to their purpose is processed
- Measures to limit the impact of cyber attacks including the protection of key functionality
- Measures to minimise any potential negative impacts on other networks or devices
- Measures to limit attack surfaces
- Appropriate event logging implemented
- Functionality to enable users to delete or transfer their data.
The essential cyber security requirements also state that manufacturers of PDEs shall have specific vulnerability handling processes, including:
- An inventory of PDE components and vulnerabilities
- Procedures to remediate identified vulnerabilities without delay
- Regular reviews and tests of PDE security
- Procedures for communicating information on identified vulnerabilities
- Procedures for distributing updates to resolve vulnerabilities.
CRA Obligations For Different Entities
Under the CRA, various stakeholders involved in the lifecycle of PDEs (including manufacturers, importers, distributors, and open-source software stewards) each have distinct roles, responsibilities, and obligations to ensure the cybersecurity of these products.
Let’s break down what each group is expected to do, and the requirements they need to meet.
Manufacturers
To comply with the CRA, PDE manufacturers must ensure that cyber security is a key factor in the planning, design, development, production, delivery and maintenance of the PDE. The cyber security risks of the PDE must be documented, and any actively exploited vulnerabilities and serious incidents for PDE formally reported. For the duration of a PDE's support period, the manufacturer must ensure that vulnerabilities are effectively managed, and that security updates are made available to users during the PDE’s agreed period of use. The manufacturer also needs to ensure that the PDE has clear and understandable instructions for use, and that it meets all essential cyber security requirements.
Importers and distributors
The CRA imposes a number of due diligence responsibilities upon PDE importers and distributors. PDE importers must ensure that the PDE manufacturer has met its obligations under the Act, including that it is compliant with all essential cyber security requirements, that the appropriate conformity assessment has been completed, and that technical documentation has been produced. PDE distributors are required to verify that both the manufacturer and importer have met their key CRA obligations. Finally, both importers and distributors need to ensure that the PDE bears a CE marking, and that any risks or vulnerabilities they identify are appropriately reported.
Open-source software stewards
Whilst the CRA does not apply to open-source software made available outside the scope of commercial activity, it does introduce limited obligations for what it terms ‘open-source software stewards’. These stewards are defined as legal entities (other than a manufacturer) that provide ongoing support for the development of specific PDEs qualifying as free and open-source software intended for commercial activities, and ensure these products’ long-term viability.
The Act requires open-source software stewards to implement a cyber security policy to foster the secure development of PDEs and the effective management of vulnerabilities by developers. Where applicable, these entities will also need to ensure vulnerabilities and serious incidents related to PDEs are appropriately reported.
Relationship to the AI Act
As mentioned previously, the CRA is designed to complement other existing EU regulations, and one key example is the EU Artificial Intelligence (AI) Act. PDEs that are classed as high-risk AI systems under the AI Act will be considered compliant to its cyber security requirements (Article 15 - Accuracy, robustness and cybersecurity) provided that they meet the CRA’s essential cyber security requirements, and that this can be evidenced by the PDE’s CRA declaration of conformity.
Noncompliance and Enforcement
Noncompliance with the CRA can lead to significant penalties that scale with the severity of the violation. Manufacturers that commit the most serious violations, i.e., noncompliance with the essential cybersecurity requirements or their key obligations, can be fined up to €15 million or 2.5% of worldwide annual turnover, whichever is higher. For other key violations, organisations (including importers and distributors) can be fined up to €10 million or 2% of worldwide annual turnover, whilst the supply of incorrect, incomplete or misleading information to authorities can lead to fines of up to €5 million or 1% of worldwide annual turnover.
UK Applicability
The CRA's requirements apply to any PDEs placed on the EU market. This means that UK organisations intending to sell their products on the EU market, either directly or via a third party, will need to ensure that they comply with the CRA's requirements.
The closest equivalent to the CRA in the UK is the Product Security and Telecommunications Infrastructure Act (PSTI), which entered into force in April 2024. The PSTI aims to ensure that consumer connectable products are developed with features that protect them from cyber attacks and that safeguard user privacy and data, and its scope covers ‘relevant connectable products’. These are consumer products that can connect to the internet and transmit and receive digital data such as smartphones, tablets, smart speakers, TVs, and cameras, connected home appliances such as washing machines and fridges, smart doorbells, baby monitors, and security cameras and wearable fitness trackers. However, the CRA is more detailed (in terms of its cyber security requirements) and wide-ranging (in terms of the in-scope products) than the PSTI.
Closing Thoughts
The CRA represents a key step forward in strengthening the EU’s digital security regulatory landscape. By clearly defining responsibilities across the supply chain and introducing meaningful enforcement measures, the CRA ensures that cyber security is no longer an afterthought but a core requirement.
How URM Can Help
If you are looking to develop your organisation’s cyber security and resilience, URM can provide flexible support that is aligned with your organisation’s objectives and requirements, as well as with best practice. This can include conducting risk assessments, helping you select and implement appropriate security controls, producing and exercising business continuity and disaster recovery plans, etc. Meanwhile, URM’s range of CREST-accredited penetration testing services allow you to proactively identify and remediate vulnerabilities within your organisation’s digital environment before they can be exploited by a threat actor.
To ensure your organisation has the fundamental cyber security measures in place that are recommended by the National Cyber Security Centre (NCSC), URM can also offer a range of services to help you achieve Cyber Essentials certification or certification to Cyber Essentials Plus, the scheme’s audited qualification. These services include conducting a gap analysis of your existing security practices against the scheme’s requirements, and providing a Cyber Essentials application review service, where we review your completed questionnaire for compliance before formal submission. As a Cyber Incident Exercising (CIE) Assured Service Provider under the NCSC scheme, we can also deliver tailored and appropriate CIE that enables you to validate your incident response plans enhance your cyber incident management capabilities.
In addition to our consultancy services, URM will be delivering a free, 1-hour webinar on Building Cyber Resilience – Practical Steps for Reducing the Likelihood and Impact of a Cyber Breach. Register for the webinar on 19 November at 11am, where we will explore practical approaches and steps along with ‘must-do’ actions to help your organisation both strengthen its defences and minimise the impact if a cyber breach were to occur.
URM is pleased to provide a FREE 30 minute consultation on penetration testing for any UK-based organisation.
If you are unsure, URM can perform CREST-accredited internal and external penetration testing against all IP addresses associated with your organisation, location, or service.
Designed to assess the architecture, design and configuration of web applications, our web application pen tests use industry standard methodologies to identify vulnerabilities.

URM’s blog breaks down the new EU Cyber Resilience Act, what products/entities are in scope, the security requirements it imposes on organisations, and more.

URM’s blog explores the importance of cyber resilience & the steps organisations can take to prepare for and mitigate the impact of a cyber incident.

URM’s blog discusses the best next steps your organisation can take following Cyber Essentials certification to further enhance its security posture.




