In this blog, we explore the National Institute of Standards and Technology Cybersecurity Framework’s (NIST CSF’s) newly introduced Govern Function, outlining its purpose and significance within version 2.0 of the Framework. We examine each of its six Categories in detail, from defining organisational context and risk management strategy to establishing oversight and supply chain risk management, and explain the policies, processes and activities you will need to implement and conduct for conformance with each Category.
As technology keeps advancing and cyber criminals come up with new ways to attack computer systems, more companies are starting to realise that cyber security should be managed just like any other business risk. In response to this, many organisations are leveraging the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) to address their own cyber security risks and demonstrate robust security capabilities to their stakeholders.
Why is the NIST CSF important?
Although the NIST Cybersecurity Framework (CSF) was originally designed as a requirement for companies managing critical infrastructure in the U.S., it has since been adopted voluntarily by organisations globally, spanning a wide range of sectors and sizes. This is because the Framework helps organisations identify and understand the most significant risks they face and focus on protecting their most important assets, instead of just going through a checklist of security task. Also, the CSF helps organisations establish how strong their cyber security is and improve it step by step. It uses a simple tier system that makes it easy to adapt, guiding them in spotting threats, protecting against them, noticing problems, responding quickly, and recovering from attacks.
What does NIST CSF consist of?
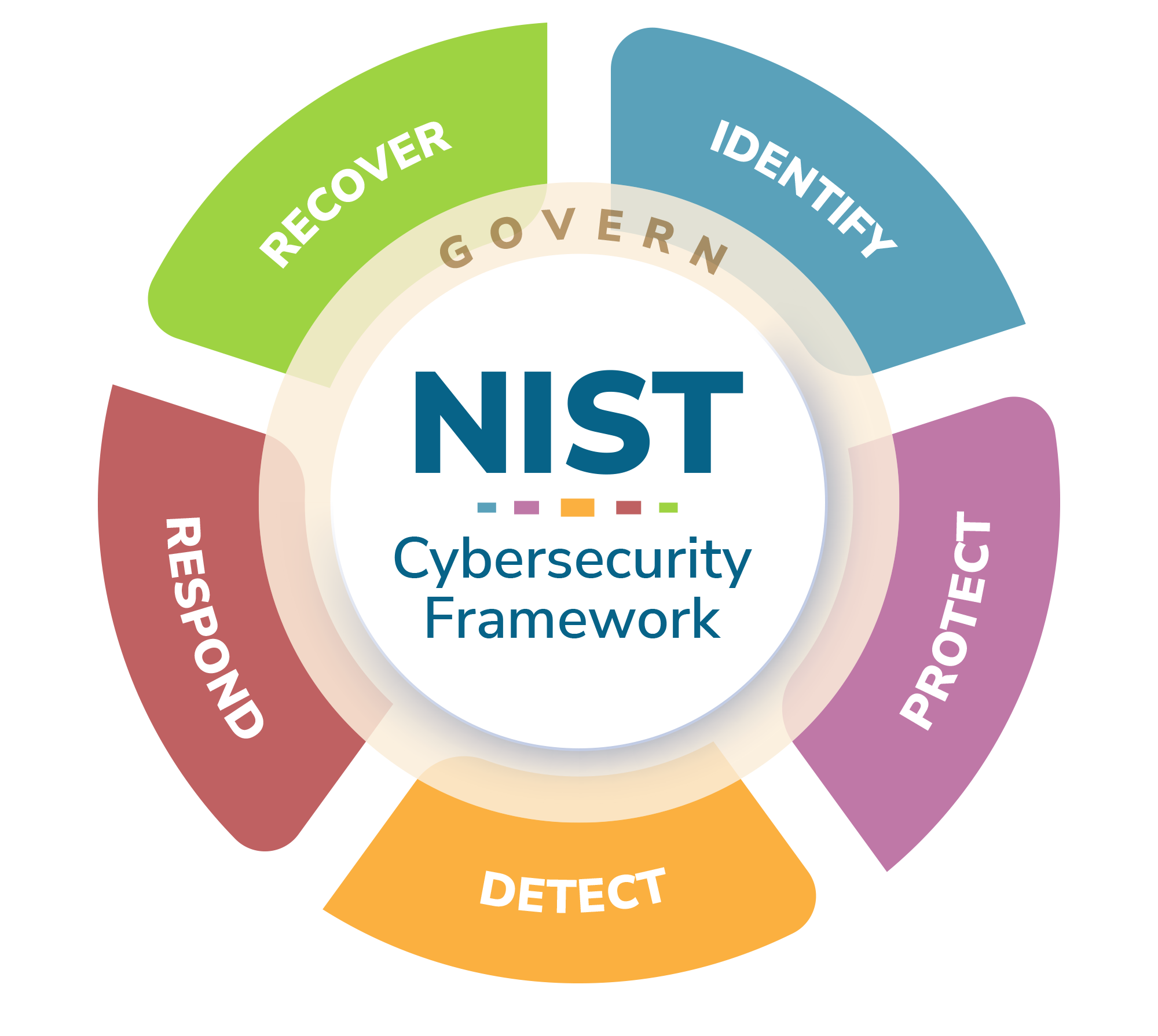
The NIST CSF has six ‘Core Functions’ (or sections) outlining the different stages of NIST’s cyber security risk lifecycle. These Functions are as follows:
- Govern: Requires organisations to define their cyber security risk management strategy, stakeholder expectations, and establish, communicate and monitor its cybersecurity policy
- Identify: Focuses on ensuring that organisations understand their current cyber security risks
- Protect: Involves implementing appropriate safeguards and controls that allow organisations to manage their cyber security risks
- Detect: Defines the activities organisations must conduct to identify and analyse cyber security attacks and compromises they face, including the use of measures such as network monitoring, physical monitoring, and hardware and software monitoring
- Respond: Supports organisations’ ability to take action when a cyber security incident is detected, using measures such as incident analysis, response, and mitigation.
- Recover: Aims to restore assets and operations that are affected by a cyber security incident, using measures such as recovery action coordination, data backup verifications, and strategic communication of incidents with stakeholders.
These Functions include a number of Categories, which are related cyber security outcomes that collectively comprise the Function in question, as well as a number of Subcategories that provide more specific outcomes of technical and management activities.
What does the Govern Function require?
The Govern Function is a relatively recent addition to the NIST CSF, having only been added in version 2.0 of the Framework, released in February 2024. However, this is not to say that the Govern Function is less important or relevant than the other five Functions; in its often-used diagram of the six Functions as a wheel, NIST always depicts Govern in the wheel’s centre, due to its foundational role in informing how the other five functions will be implemented by an organisation.
The Govern Function is focused on defining the circumstances of your cyber security risk strategy, with the aim of incorporating cyber security risk into your organisation’s overall risk management strategy. At a high level, this Function requires you to establish, communicate and monitor your cyber security risk management strategy, and ensure you understand your stakeholders’ security expectations. You also need to implement and communicate a cyber security policy that is applicable to your organisation.
The Govern Function comprises six Categories, which we will explore below.
GV.OC – Organisational Context
Organisational Context addresses your organisation’s understanding of the circumstances surrounding its cyber security risk management decisions, covering your organisation’s mission, stakeholder expectations, dependencies, and legal, regulatory and contractual requirements. So, you need to ensure you understand your organisation’s mission, i.e., what you aim to achieve through your organisational activities, which may be recorded as a written mission statement on your website or communicated via user awareness training. Your mission should also be used to define your approach to cybersecurity risk. One effective method of achieving this is through a management workshop, where managers discuss how to align your security strategy with your overall mission. For example, if a medical research company’s mission statement specifies its aim is to ‘conduct exemplary medical research that will be used to improve the health and well-being of all’, this could point to a need for the IT systems supporting such research to be well-secured, backed up, and easily restorable if an unexpected outage was to occur. Once your cyber security risk strategy has been defined, this should be regularly reviewed to ensure it remains aligned with your mission and business objectives.
You also need to define the internal and external stakeholders relevant to your cyber security strategy and their needs and expectations. This can be achieved by creating an interested parties register and reviewing this on a regular basis. If any of your external stakeholders depend on or expect you to fulfil important objectives, capabilities or services, these also need to be understood and formally communicated to relevant personnel within your organisation. Similarly, if your organisation is dependent on any specific outcomes, capabilities or services, these need to be understood by and communicated to relevant personnel. Finally, you will need to be aware of the legal, regulatory and contractual obligations relevant to security, privacy and civil liberties that you need to comply with. These obligations should be integrated into your organisation’s daily operations and reviewed on a regular basis.
GV.RM – Risk Management Strategy
This Category is focused on ensuring your organisation has established and communicated its priorities, constraints, risk tolerance and appetite statements, and assumptions, and is using these elements to support operational risk decisions.
You will need to define your risk management objectives and obtain approval from business owners or key stakeholders. You also need to produce and communicate documented statements that specify your risk appetite and risk tolerance levels, as well as your organisation’s risk response options, and develop a documented approach towards calculating, documenting, categorising and prioritising your cyber security risks.
Additionally, any cyber security risk management activities or outcomes produced should be conducted as part of your general business risk management practices (instead of being conducted separately) and be reviewed on a regular basis. Your cyber security risk strategy also needs to include the identification and characterisation of your cyber security opportunities; these are potential occurrences that would, unlike risks, have a positive impact for your organisation.
Risk Management Strategy further requires your organisation to have clearly defined communication channels so that users can report cyber security risks, including risks identified both internally and externally by your suppliers and other third parties as appropriate.
GV.RR – Roles, Responsibilities and Authorities
Here, you are required to establish and communicate roles, responsibilities and authorities relevant to cyber security risk management. This includes leadership’s responsibility for managing cyber security risk, providing resources needed in accordance with cyber security risk strategy, roles, responsibilities and policies, and fostering a culture of risk awareness, ethical conduct, and ongoing improvement. Cyber security practices also need to be incorporated into your organisation’s HR activities.
GV.PO – Policy
This Category requires your organisation to establish a cyber security policy that is communicated to personnel across your organisation, and enforced. The policy you produce will need to be regularly reviewed and updated as necessary, such as in response to changes to the threat landscape, your organisation’s requirements, etc. It also needs to be appropriate to your organisation’s context, its mission, and its goals, and personnel should be required to acknowledge the policy, so that they can be held accountable for violations of it.
GV.OV – Oversight
To meet the requirements of the Oversight Category, you will need to assess the results of your cyber security risk performance and activities, and use this information to improve your cyber security risk strategy according to the risks and needs of your organisation.
GV.SC – Cybersecurity Supply Chain Risk Management
Cybersecurity Supply Chain Risk Management focuses on identifying, establishing, managing, monitoring and improving your cyber security supply chain risk management and improvement processes. Such processes need to be part of your enterprise-level risk strategy, and include a supply chain security risk management programme, strategy, objectives, as well as appropriate policies and processes. Supply chain risk actions must be conducted by relevant stakeholders. Additionally, cyber security roles and responsibilities relevant to your suppliers, customers or partners need to be defined and communicated both within and outside your organisation. Having identified your suppliers, you will need to prioritise them according to their criticality, using specific criticality criteria. These criteria need to be based on:
- The sensitivity of data involved (i.e., data classification)
- The level of access third parties will have to the data
- The criticality of the products and services they offer.
The roles of suppliers and other third parties need to be defined, as appropriate, within your incident management processes. This should include the specific actions and activities to be carried out during the planning, response, and recovery phases of an incident.
Prior to entering a relationship with a supplier or other third party, you are required to conduct some form of due diligence assessment, which must include identification of risks relating to these third parties. These risks may arise from the suppliers and third parties themselves, as well as from the products or services they offer. Any risks identified prior to or during a supplier/third party relationship need to be formally recorded, prioritised, assessed, responded to and monitored by your organisation. When responding to these risks at any stage of the relationship, the requirements to address them should be established, prioritised and integrated into your third-party agreements as appropriate. In addition to managing supply chain cyber security risk before and during the relationship, your organisation must also establish plans for handling any related cybersecurity risks once the relationship has concluded.
Finally, as referred to above, supply chain security practices need to be integrated into your organisation’s cyber security and enterprise-level risk management programmes. The performance of these activities needs to be monitored throughout the technology product and service life cycle (i.e., when managing ICT products and services).
Closing Thoughts
As cyber threats grow more complex, the NIST CSF offers you a structured way to manage cybersecurity risk. At the heart of the Framework is the Govern Function, which is essential if you want to align with NIST CSF. It challenges you to tailor your cybersecurity risk programme around your organisation’s mission, resources, and existing practices. By placing governance at the centre, the Framework emphasises that cybersecurity should be embedded into your overall strategy and not treated as a separate issue.
How URM can Help
Consultancy
With 2 decades of experience helping organisations align with major information security standards and frameworks, URM is the ideal partner to provide NIST CSF consultancy services to support your organisation with any aspect of its conformance with Framework. Our large team of experienced NIST CSF consultants can offer your organisation a wide range of consultancy services to help you meet the NIST CSF requirements in full; for example, we can begin by conducting an NIST gap analysis, where we establish where you are already conformant, and those areas which may require further improvement. Following the gap analysis, we can support your CSF implementation by assisting with all of the 7-step implementation process, or with specific steps as required.
Once you have implemented the Framework, URM can also provide NIST CSF 2 assessment services. These involve your dedicated NIST CSF consultant conducting independent, impartial assessments of your organisation’s conformance, covering the Categories and Subcategories within the Framework’s six Core Functions. Here, we will assess the maturity level of controls implemented by your organisation, determining a current maturity score based on NIST’s maturity scale, identifying improvements that could be made, and providing a predicted maturity scores following completion of recommended improvements.
URM is pleased to provide a FREE 30 minute consultation on penetration testing for any UK-based organisation.
If you are unsure, URM can perform CREST-accredited internal and external penetration testing against all IP addresses associated with your organisation, location, or service.
Designed to assess the architecture, design and configuration of web applications, our web application pen tests use industry standard methodologies to identify vulnerabilities.

URM’s blog breaks down the NIST CSF’s new Govern Function, its importance, and the policies, processes and activities you will need to have in place to comply.



