In this blog, we explore how ransomware attacks occur, why they represent a significant threat to organisations of all sizes, and the practical steps your organisation can take to reduce the risk and strengthen its cyber resilience. We highlight the importance of addressing people, processes, and technology, and explain how adopting frameworks like Cyber Essentials or ISO 27001 can provide a structured foundation for building resilience against ransomware.
Ransomware is, unfortunately, a term that many of us are becoming more and more familiar with. Often present in news articles, there is an ever-increasing number of stories covering both ransomware victims and ransomware gangs. It is one of the most dangerous cyber threats organisations currently face, capable of halting operations, compromising sensitive data, and causing significant financial and reputational damage.
Understanding Ransomware
Put simply, ransomware is a type of malicious software (malware) that aims to hold the user’s data at ransom, making it unavailable unless a demand is met. This is often achieved by encrypting the data, with decryption offered once a payment has been received. In a number of cases, the ransomware actor will threaten to leak the data if payment is not received within a certain timeframe.
How Do Ransomware Attacks Occur?
Ransomware attacks start with a compromise of your systems. Such compromise can be the result of a variety of actions, such as:
- Exploitation of a public-facing web application
- Use of compromised credentials
- An individual within your organisation clicking on a malicious phishing email
- Vulnerability within your supply chain.
Once a threat actor has succeeded in compromising your system, ransomware will be deployed. This begins the process of encrypting data, making it inaccessible to the target. Typically, the threat displays a ransom note, instructing the victim on how to pay the ransom in order to receive the decryption key. Whatever approach is taken, the ultimate aim is to gain control of your data and demand a ransom. More recently, the methods used to threaten or scare the victims into paying the ransom have evolved, including threatening to publish/leak data, notify the victim’s regulator, and threatening senior management.
What Can Be Done to Stop Ransomware?
There are three key areas in which your organisation can look to bolster its defence: people, processes and technology. To mitigate the risk of ransomware, it is important to understand and treat the risks associated with these. Due to their interconnection, it is best to have a holistic approach, as opposed to only focusing on one area. You will also benefit by scrutinising the security of third parties within your supply chain as part of this, as your supply chain is effectively an extension of your organisation and must be accounted for when it comes to security (to learn more about effective supply chain security risk management, read our blog on Common Questions When Managing Supplier Information Security Risks). But let us focus on the three pillars of people, processes and technology.
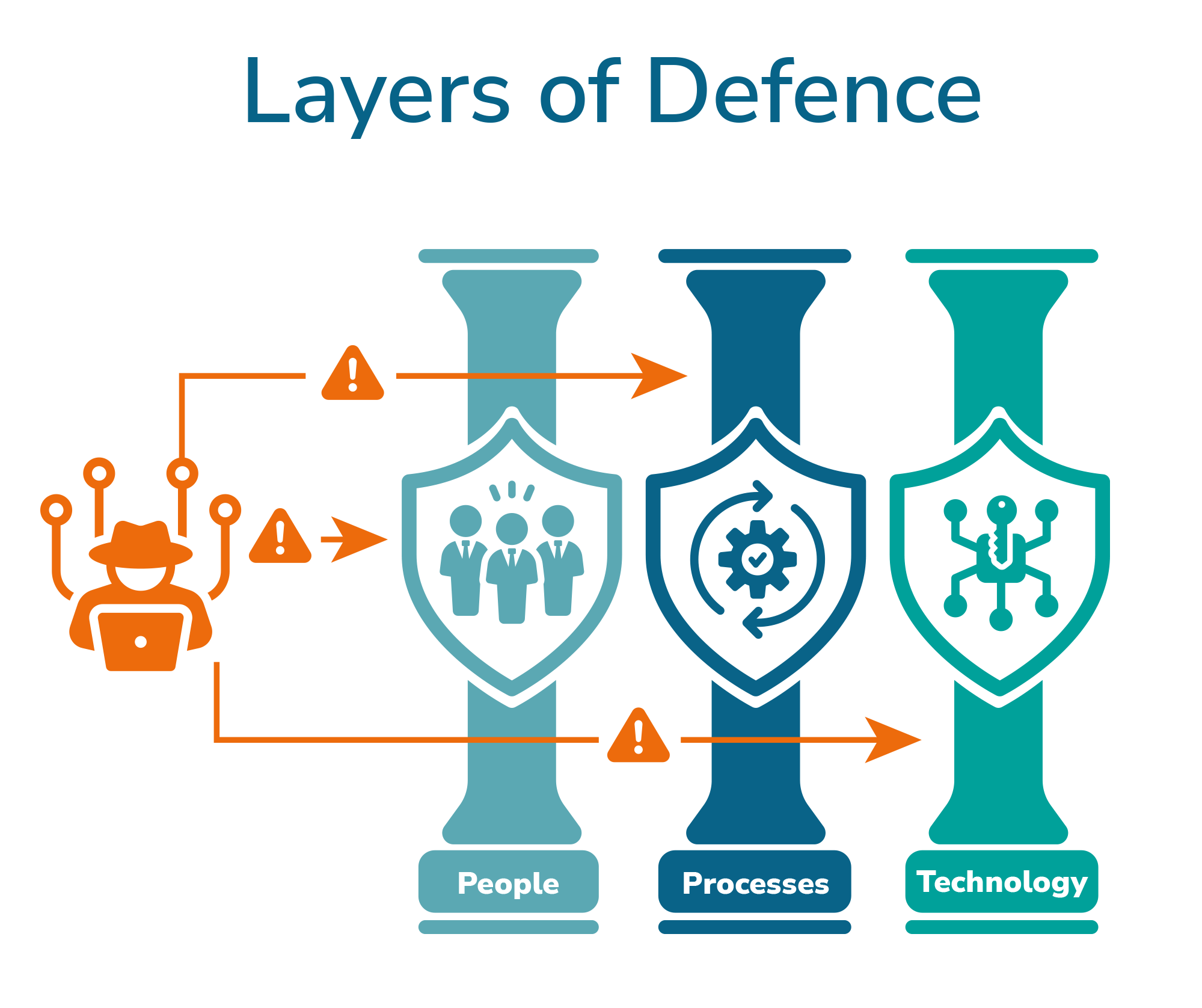
People
Organisations will often mistakenly assume that only those working in information security have responsibility for maintaining it; however, any person in your organisation is a potential point of exploitation and, as such, effective information security is a collective responsibility. For example, it is essential that all staff have been trained on how to identify and report phishing emails, as anyone with an organisational email could receive one.
The most effective way to mitigate the risk of ransomware when it comes to people is to provide interactive information security and awareness training that aims to educate employees on their responsibilities, and provide information on current threats and how to deal with them. This training should go beyond a simple box-ticking exercise and be tailored to your organisation’s specific risks and threat landscape. Awareness training also provides an opportunity for employees to ask questions and raise concerns. To enhance understanding, training can be supplemented with activities such as phishing simulations.
Processes
When we refer to processes, we are looking at any actions taken to achieve a particular purpose, aim or output. They can incorporate both people and technology; for example, implementing a process that requires employees to use multi-factor authentication (MFA) to access systems, or a policy that outlines how to create strong passwords.
One of the most important processes for increasing resilience against ransomware is a backup process that is both tested and regularly performed. Whilst this does not necessarily preserve the confidentiality of compromised data, it does help your organisation to ensure the availability of that data as much as possible in the event of a ransomware attack.
When looking to mitigate the likelihood and impact of ransomware attacks, your organisation should consider implementing the following processes:
Technology
Technology-based security measures can be used to complement both people and process-based measures. For example, using technology that requires MFA adds another layer of defence if an individual’s account credentials are compromised.
One of the easiest ways for attackers to gain unauthorised access to your organisation’s systems is by exploiting known vulnerabilities, so it is essential to ensure that you use supported technology with the latest security patches installed. Other technological measures and solutions that can help protect your organisation against ransomware include:
- Endpoint detection response to detect, investigate and respond to threats on endpoints such as laptops
- Firewalls to filter traffic on the network and prevent unwanted traffic
- Antivirus to detect and quarantine or remove malware
- Intrusion detection and prevention systems to detect early signs of compromise and prevent further intrusion
- Network segmentation to limit an attacker’s ability to move around your network
- Mobile device management to enable the latest patches to be applied as well as device wiping when required
- Regular penetration tests and vulnerability scans to identify and treat weaknesses in your IT environment before they can be exploited.
Where Do You Start?
Given the vast range of possible countermeasures, knowing where to begin in protecting your organisation from ransomware can be a challenge. One effective starting point is to adopt a recognised cybersecurity framework or certification scheme, which can provide clear structure and direction for building your cyber resilience strategy. For instance, achieving Cyber Essentials certification helps you implement a core set of baseline security controls, offering protection against around 80% of the most common cyber threats.
For a more comprehensive, risk-focused approach, ISO 27001 (the International Standard for Information Security Management Systems) enables your organisation to identify, assess, and prioritise security risks, including those associated with ransomware. This risk-based methodology supports informed decision-making and resource allocation, ensuring that you focus on the areas of greatest potential impact. ISO 27001 also defines a range of controls spanning people, processes, and technology (such as ongoing security awareness training, formal incident response procedures, supply chain risk management, and the implementation of robust information security policies) all of which help to reduce both the likelihood and impact of a ransomware attack.
How Can URM Help?
With our broad range of cyber and information security consultancy services, URM is the ideal partner to support your organisation in strengthening its resilience to ransomware, or in enhancing its cyber security posture more generally.
As an accredited Cyber Essentials certification body, we have been involved with hundreds of successful Cyber Essentials and Cyber Essentials Plus assessments, enabling us to both facilitate your assessment and help you prepare. We can conduct a gap analysis to identify any areas of noncompliance, and conduct Cyber Essentials application review to ensure your answers to the self-assessment questionnaire (SAQ) meet the scheme’s requirements. We are also a Cyber Incident Exercising (CIE) Assured Service Provider under the National Cyber Security Centre’s (NCSC’s) scheme, allowing us to deliver CIE services that are fully aligned with the NCSC’s high standards.
To identify exploitable vulnerabilities within your organisation’s IT environment, URM can provide CREST-accredited penetration testing against all assets associated with your organisation, location or service. Depending on your needs, we can offer network and infrastructure penetration testing, web or mobile application pen testing, cloud pen testing, and business-led penetration testing. In addition, all of our CREST penetration testing includes a free retest within 30 days of the original assessment of any high or critical-risk vulnerabilities identified, allowing you to ensure the greatest security risks are mitigated quickly.
If your organisation would benefit from developing its security programme further with a more advanced security framework, URM can leverage its 20-year history of providing ISO 27001 support to help you achieve and maintain certification to the Standard. Our experts can support you through all stages of the Standard’s lifecycle, from conducting an ISO 27001 gap analysis and risk assessments through to ongoing management system and control audits, with all the guidance and assistance we provide being fully tailored to your organisation’s unique culture, style and needs.
From BIAs to bespoke BC plans and ISO 22301 certification, our expert consultants can help you build resilience. Let URM support you with proven tools, tailored advice, and practical solutions to protect what matters most.
We’ll help you develop and test robust BC plans, conduct BIAs with our Abriska® 22301 tool, and close any gaps. Partner with URM to meet ISO 22301 standards and protect your operations from disruption.
Strengthen your response with challenging, scenario-based BC exercises. URM will assess your team’s performance, identify gaps, and provide actionable insights to help improve resilience and readiness for real-world disruption.

URM’s blog discusses how to develop and implement an information security policy that fully conforms to both your organisation’s and ISO 27001 requirements.

Typically, this question is twofold; which assets to include and the depth or granularity. In this blog, we will look at granularity.

URM’s blog explains the legal, regulatory & contractual controls in ISO 27001 & how they can be implemented in full conformance with the Standard.



