Table of Contents
The majority of us have heard the acronym ‘CIA’ being thrown into conversations when discussing information security, but what does it actually mean? When used in the context of information security, CIA refers to confidentiality, integrity and availability, the three key principles that together provide the appropriate basis for implementing and managing information security as well as the associated policies.
In this blog, we will establish what each of these individual aspects represent in the context of information security.

Confidentiality
The definition of confidentiality as stated in ISO/IEC 27000:2018:
“[the] property that information is not made available or disclosed to unauthorized individuals, entities or processes”.
In plain English, this means that access to information should be managed, protected and controlled so that it is only accessible to authorised processes, individuals or entities and that the type of access is appropriate to the type of information and the purpose(s) for which access is required. For example, documents which only contain publicly-available information can be marked as ‘public’, published on your organisation’s website, and made accessible to everyone. Meanwhile, documents containing confidential information should only be made available to managers and executives or selected individuals using role-based access controls (RBACs), which grants access based on project roles or managerial responsibilities.
This is particularly relevant for the accessing of sensitive or personal information and aligns with the ISO 27001:2022 requirement for the classification of information, as well as the ‘need to use’, ‘need to access’ and ‘least privilege’ principles found in ISO 27002:22. Under the ‘need to use’ principle, access to resources is only granted to individuals if it is necessary for the performance of their role, while ‘need to access’ expands on this idea to include access to sensitive data and information, with access only being granted based on individuals’ roles and the information they need for specific tasks. The ‘least privilege’ principle suggests that individuals or systems should only have the minimum amount of access they need to do their jobs.
Integrity
The definition as specified in ISO/IEC 27000:2018 is:
“Integrity is the property of accuracy and completeness”.
In the context of information and data, it means that it needs to be consistent, accurate and trustworthy in terms of its content and detail throughout its entire lifecycle. If the integrity of information and data is compromised in some way, this can have significant consequences for the individuals, organisations or systems involved in handling it, such as reputational damage, financial loss, legal and compliance issues, etc. Controls and protection such as encryption, user access controls, backup and recovery procedures etc., should be applied to ensure that it is not altered or changed by unauthorised persons or processes, and this particularly applies to information and data in transit. If the accurate processing is particularly important to your organisation, specific checks of information integrity can be added to the information processing lifecycle, such as input and output validity checks.
Availability
The definition of availability given in ISO/IEC 27000:2018 is:
“the property of being accessible and usable on demand by an authorised entity”.
What this means in terms of information security and resilience is that information should be consistently and readily accessible so that the authorised entities (e.g., people, processes, etc.) can carry out the activities necessary for the performance of their role, as and when they are required. If the necessary information isn’t readily available to individuals, this can hinder their ability to do their jobs. For example, if an employee’s account has a problem, they may not be able to access the necessary information to finish their work. You should, therefore, implement and configure appropriate infrastructure to ensure that this can be done on demand or as scheduled.
The availability principle also requires all supporting hardware, systems, services and technical infrastructure to be appropriately maintained to ensure that these required properties are retained for the systems that hold, process and display information.
For some high availability systems, it is important that failures are prevented, and this can be achieved by ensuring they have been built with resilience and redundancy functions. A resilient system has the capacity to withstand and bounce back from disruptions or failures and can continue to operate when faced with unexpected challenges. Redundancy, on the other hand, involves duplicating important parts or functions in a system to have backup or alternative resources in order to avoid a single point of failure.
What does this mean in a practical sense in terms of implementing controls?
These three principles form the basis for establishing an effective information security framework. Although they support some aspects that may not initially seem relevant to information security, if you adopt a comprehensive approach to information security which includes CIA you will be on course to have an effective information security management system (ISMS).
As an example, if you identify that certain information has a requirement for confidentiality, this implies that the information has to be protected to an extent that is outside the norm. By default, you will then need to implement controls and protective measures to ensure that the confidentiality requirement is enforced. Mechanisms that can help provide the necessary levels of confidentiality include:
- Role based access controls (RBACs) – as mentioned above, RBAC provides access to information on a need-to-know basis and the type of access is also controlled, e.g., read only, modify, update, full access, etc.
- Encryption of the information – whether at rest or in transit, the information is unreadable unless the entity, process or individual has been provided with the appropriate encryption key(s) to access the information in its decrypted form
- Multi-function authentication (MFA) – organisations implementing MFA have taken additional steps to ensure the confidentiality of information by establishing additional requirements to authenticate users who are attempting to access it
- Secure communication channel – organisations implementing secure communication solutions such as secure file sharing, secure email, SFTP etc., can help prevent unauthorised access to confidential information
- Data masking – data masking involves safeguarding sensitive data, such as personally identifiable information (PII) or financial data, by obscuring or substituting it with fictional or altered data. This ensures that the data remains usable for testing, development, or other non-production purposes.
It should be noted that the need for confidentiality may also be required to meet legal, regulatory and/or contractual obligations and that non-compliance can result in litigation, imposition of fines or termination of contract. For example, the General Data Protection Regulation (GDPR) requires you to maintain the confidentiality of the personal data you process, in order to keep it secure from internal or external threats.

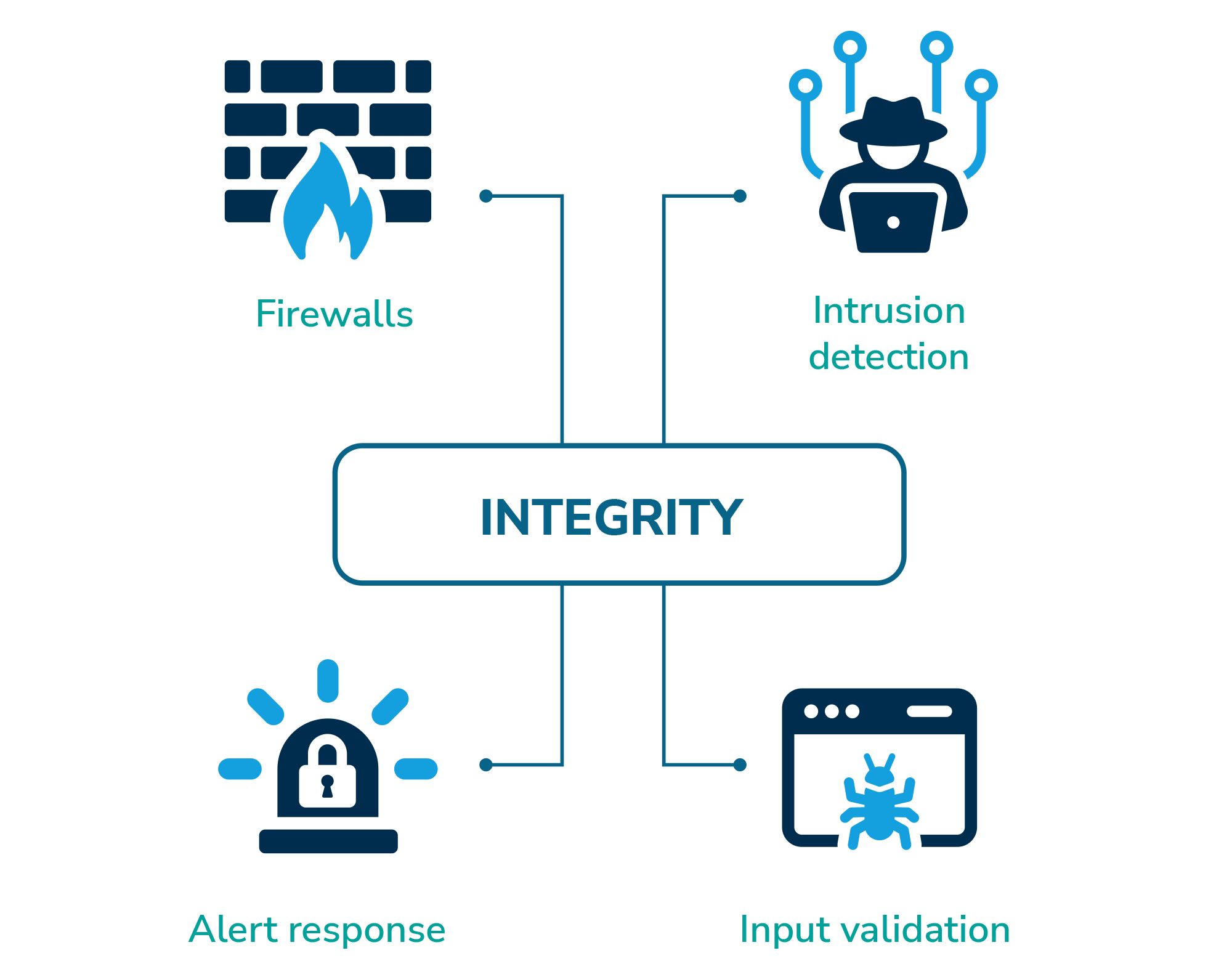
The principle of integrity requires that information is not modified or tampered with at any time, whether at rest or in transit, and that it is accurate and complete. To ensure that you have adequately addressed this principle, it is essential that you implement appropriate controls. These controls can include:
- Implementing firewalls – these should be suitably configured to prevent external parties from gaining access to information, modifying it or making it unavailable to the organisation
- Intrusion detection – this can be both from a physical security and a technology perspective. Both systems can deliver alerts following attempts to access information or premises by unauthorised entities
- Controls and procedures for responding to alerts – for example, incident response plans
- Input validation – this can help ensure that user inputs are examined and validated, mitigating the risk of common security vulnerabilities, including SQL injection, cross-site scripting (XSS), and other types of injection attacks.
Your organisation’s ability to provide assurances that the information it holds, processes and provides is accurate and complete is essential for the continued trusted operation and interaction with customers and regulatory bodies.
Finally, we need to examine the principle of availability. This principle includes resources (e.g., financial, people, premises, etc.). When addressing the organisation’s requirements for availability, attention should be given to determining what needs to be done to identify the requirements for availability and how best they can be met. A business impact analysis (BIA) can help you with this, as you can use the BIA to understand your organisation’s critical functions, evaluate the possible effects of disruptions, and establish criteria for maintaining or restoring availability. Controls and actions to deliver the identified availability requirements include:
- Resilient infrastructure configurations – this includes aspects such as redundant array of independent disks (RAID), dual routing for essential services, redundant environmental controls, e.g., air conditioning units with dual compressors, etc.
- Failover configurations – when primary services fail, failover to secondary services is activated. In some instances, this can be automated, depending on the configurations employed
- Cross-training of personnel – by cross training staff, organisations can ensure that should any key individual or group of individuals be unable to complete their duties for whatever reason, suitably skilled resources are available from within the organisation to ensure continued delivery of the activity, albeit at a potentially reduced level of performance
By addressing these key principles when developing, implementing, managing and maintaining information security, the organisation will be well-placed to satisfy the majority of operational, legal, contractual and regulatory obligations.

How URM can help
Having assisted over 400 organisations with their ISO 27001 certification, without a single failed certification project, URM is ideally placed to help your organisation develop and implement an ISMS that is based on the principles of CIA and aligns with the requirements of the Standard. Our large team of ISO 27001 consultants can offer support with any aspect of conformance to the Standard that you require, whether that be full lifecycle services or help in a more specific area, such as conducting risk assessments or policy/process development. As well as this, we can conduct an ISO 27001 internal audit on your behalf to help you ensure the ISMS is being properly maintained and operating effectively. The consultant who conducts your ISO 27001 audit will be capable and competent, but also impartial, allowing you to meet the auditing requirements of the Standard in full after you have certified.
Alongside our consultancy services, we can offer a wide range of training courses, all led by a qualified and practicing ISO 27001 consultant. URM’s ISO 27001 training courses are suited to individuals who are just starting out with the Standard, and for those with more experience who need help transitioning to ISO 27001:2022.
URM is pleased to provide a FREE consultation on Transitioning to ISO 27001:2022 for any UK-based organisation.
URM can help you achieve ISO 27001 certification
URM can provide a range of ISO 27002:2022 transition services including conducting a gap analysis, supporting you with risk assessment and treatment activities as well as delivering a 2-day transition training course.

2nd part of question and answer session where URM compared and contrasted 2 of the world’s leading information security standards, ISO 27001 and SOC 2.

Typically, this question is twofold; which assets to include and the depth or granularity. In this blog, we will look at granularity.

A key role of risk management is helping organisations decide how limited resources can be most effectively used to address the most pressing business issues.

