Table of Contents
ISO 27001, the World's leading Information Security Management Standard, was revised in October of 2022, and our blog Transitioning to ISO 27001:2022 provides practical guidance on meeting the new requirements.
The introduction of the threat intelligence control into the new Standard, we believe, requires careful consideration among organisations which have already achieved ISO 27001 certification, due to the required risk assessments in Clause 6.1, which implicitly require you to consider information security threats. This means that the selection of Control 5.7 in your Statement of Applicability (SoA) is virtually unavoidable. For most organisations, the inclusion of this control helps to formalise the collection and analysis of threat information, which is a key component of the risk assessment process detailed in Clause 6.1.
Changes to Risk Assessment
The requirements of this new control suggest that there needs to be a more proactive approach to risk management and threat analysis. Risk assessments will now need to be updated in response to any threat intelligence that is received and, following an analysis of this intelligence, found to be impactful on information security. Assessors will be looking for shortcomings in the effective collection and analysis of threat intelligence.
Collecting and Analysing Threat Intelligence
A key piece of information to take from this is that your organisation does not need to spend excessive amounts of money on threat intelligence services as there are multiple and varied sources of threat information available such as specialist threat intelligence forums, information security organisations (such as the National Cyber Security Centre, or NCSC), and information security news sites. In addition to this, the majority of vendors are proactive in notifying users of security threat information that they become aware of. The issues assessors have noted when auditing this control mainly relate to the organisation’s use of the information that they are given by threat intelligence sources.
Generally, organisations take threat intelligence very seriously and are now becoming more proactive in their approach due to the introduction of Control 5.7, but there are still numerous organisations that collect information on information security and think this alone means they’re doing enough to satisfy the requirements of the Standard. This is not the case, as organisations are not only required to collect this information, but to analyse it also.
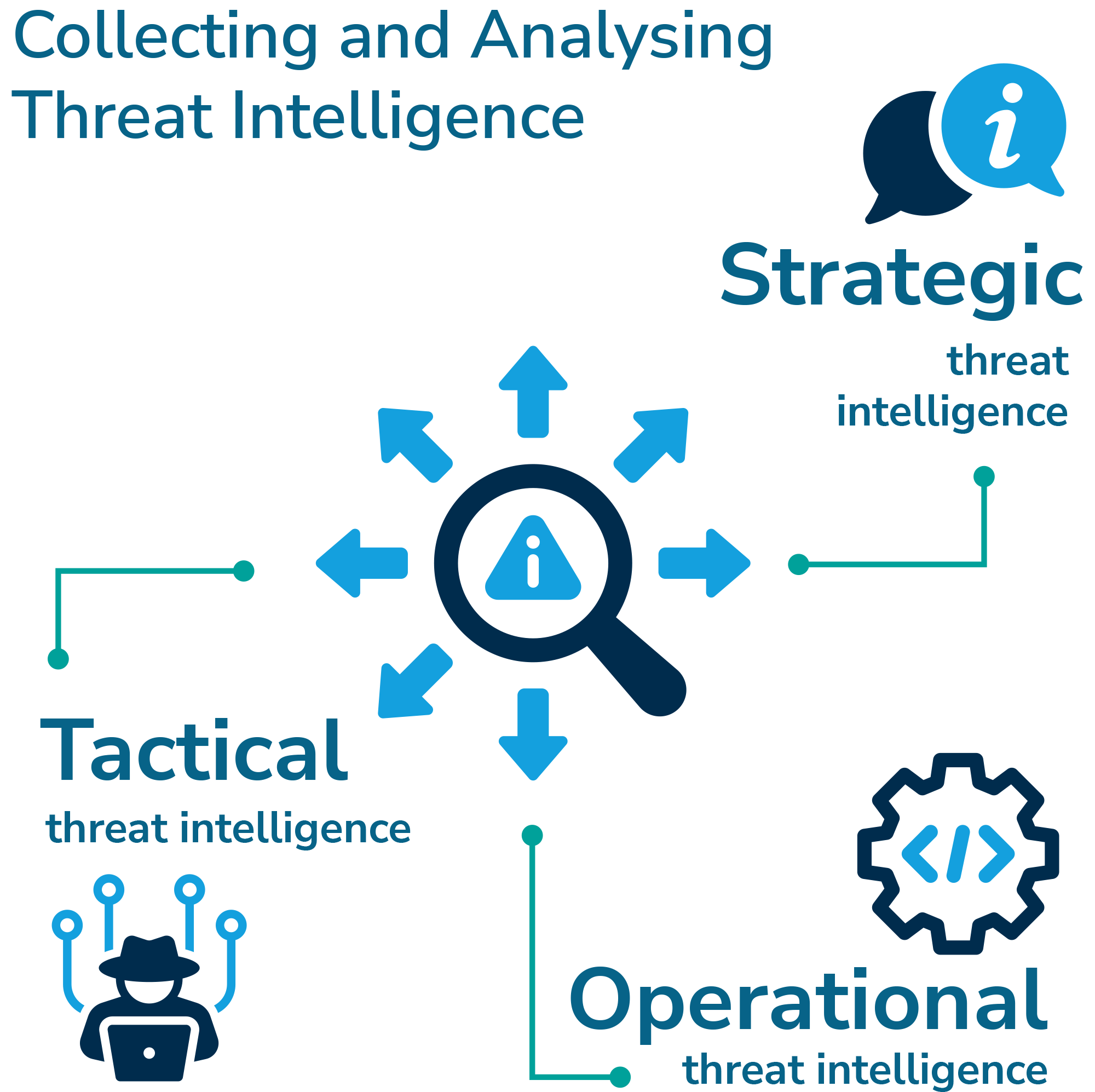
ISO 27002, which is largely seen as an ‘information security best practice guide’, divides threat intelligence into three distinctive layers:
- Strategic threat intelligence: exchange of high-level information about the changing threat landscape (types of attackers, types of attacks, etc.)
- Tactical threat intelligence: information about attacker methodologies, tools and technologies involved
- Operational threat intelligence: details about specific attacks including technical indicators.
It is key to meeting the requirements of this Control that organisations are aware of and understand the different types of threat intelligence, as well as the need for sharing that information with the relevant stakeholders, both internally and externally. By ensuring that you have a clear understanding of the types of threat intelligence, you can identify and implement appropriate mitigation measures where necessary.
Strategic threat intelligence relates more to long-term goals and behaviours your organisation wants to achieve and implement, whereas tactical threat intelligence is focused on the present impacts that threats can have and how they should be mitigated. In addition to this, there is a similarity between operational and tactical threat intelligence in that they are both focused on the present dangers to the organisation, however, operational threat intelligence has a larger focus on specific attack vectors and technological alerts to reduce the risk of an attack.
For a comprehensive analysis of threat information, you should determine the relevance of identified threats to your organisation, and one way you could achieve this is by using a risk assessment to determine likelihood and impact. You should also try to ensure the threat information is accurate by verifying the source. In addition, you should consider the context in which a threat has been seen to impact other people, organisations, or systems it has infiltrated. Finally, after your analysis of the threat information, your organisation should determine the need for action in response to the threat and ensure that any mitigation measures are swift and effective.
How Threat Intelligence Should Be Managed Within your Organisation
To ensure that your organisation is meeting the requirements of this control and is able to provide enough evidence of this to an assessor, it would be beneficial to establish threat intelligence related objectives and record the vetting of threat intelligence information sources as part of a management review/risk assessment discussion. You should also consider analysing the effects that new threats, identified through threat intelligence, will have on risks facing the organisation, and keeping records of communication of threat intelligence information to relevant interested parties, both internally and externally.
Not only does obtaining and using threat intelligence allow you to detect and respond to cyber-attacks more quickly, but it can also allow you to identify attack vectors before the attacks occur, therefore reducing the overall risk of damage to your information assets. There is also a clear commercial benefit to the effective use and analysis of threat intelligence; by responding faster to incidents and reducing the likelihood of attack, your organisation will enhance its reputation, not only in your sector, but in sectors that may be looking to use your services.

In summary, the key takeaways from this blog on threat intelligence are that:
- It is not enough to have a subscription to threat intelligence platforms, you need to do something with this information
- An assessor will be looking for evidence that threat intelligence information has been considered and reviewed alongside existing risks
- You don’t have to spend exorbitant amounts of money on threat intelligence services or platforms, there are plenty of free forums and subscriptions available
- Establishing threat intelligence objectives ensures the organisation is clear on what it needs to achieve from threat intelligence, what types of intelligence it needs to gather, how it is going to analyse and then use this intelligence and, finally, how it is going to measure the effectiveness of this process
- Organisations should make use of ISO 27002 as it is a best practice guide for the implementation of ISO 27001.
How URM can Help
If you or your organisation would like assistance in implementing not only threat intelligence controls, but also the entire ISO 27001:2022 framework requirements, URM’s large team of experienced ISO 27001 consultants can offer you reliable guidance and support. With nearly 2 decades of ISO 27001 consultancy experience, URM is adept at supporting organisations at every stage of the Standard’s lifecycle, from conducting gap analyses and risk assessments, all the way through to implementation support and conducting the ISO 27001 internal audit. For organisations looking to transition their ISMS to the 2022 version of the Standard, we also offer an ISO/IEC 27001:2022 Transition training course, led by an experienced and practising ISO 27001 consultant.
URM is pleased to provide a FREE consultation on Transitioning to ISO 27001:2022 for any UK-based organisation.
URM can help you achieve ISO 27001 certification
URM can provide a range of ISO 27002:2022 transition services including conducting a gap analysis, supporting you with risk assessment and treatment activities as well as delivering a 2-day transition training course.

A key role of risk management is helping organisations decide how limited resources can be most effectively used to address the most pressing business issues.

In this blog, we’ll take a look at management commitment, one of the most significant.

URM’s blog outlines the 6 of the key steps you can take to successfully implement an ISO 27001 conformant information security management system.

